Known MOVEit Attack Victim Count Reaches 2,618 Organizations
Data Breach Today
NOVEMBER 20, 2023
77 Million Individuals' Information Exposed, as More Victims Continue to Be Counted Trackers of the tally of individuals affected by the Clop ransomware group's mass hack attack on MOVEit servers added another 4.5 million patients' data to the ever-ascending total. The incident currently affects more than 2,600 organizations and 77 million individuals.



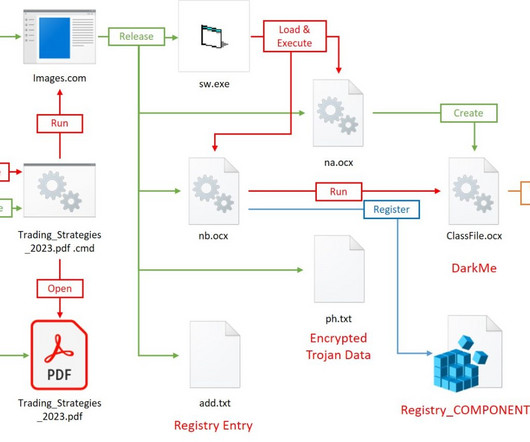






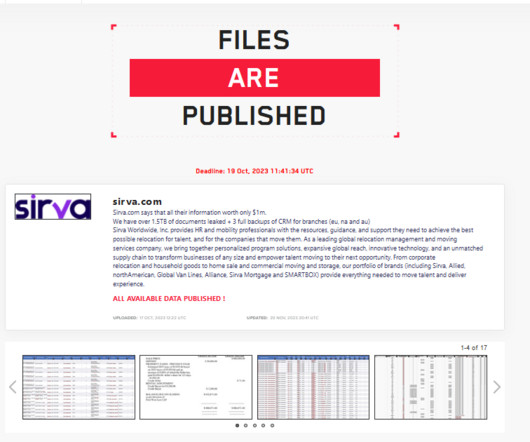


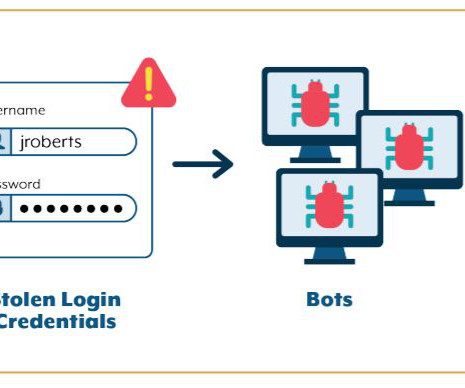




























Let's personalize your content