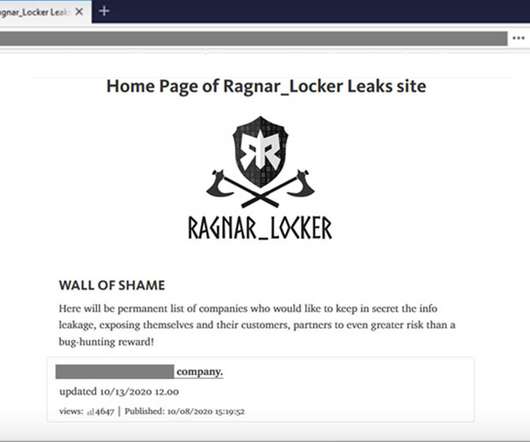
APT Groups Target Firms Working on COVID-19 Vaccines
Data Breach Today
NOVEMBER 13, 2020
Microsoft Says Attacks on Seven Companies Blocked Three state-sponsored advanced persistent threat groups - one Russian, two North Korean - have been targeting companies across the globe involved with COVID-19 vaccine and treatment development, Microsoft says.






































Let's personalize your content