Alphv group claims the hack of Clarion, a global manufacturer of audio and video equipment for cars
Security Affairs
SEPTEMBER 24, 2023
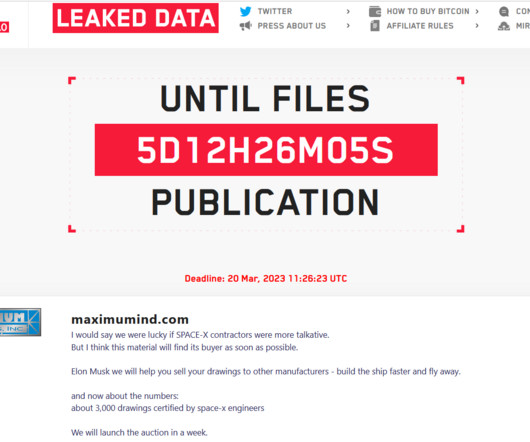
The Alphv ransomware group claims to have hacked Clarion, the global manufacturer of audio and video equipment for cars and other vehicles. The Alphv ransomware group added Clarion, the global manufacturer of audio and video equipment for cars and other vehicles, to the list of victims on its Tor leak site.














































Let's personalize your content