BlackCat Ransomware gang stole secret military data from an industrial explosives manufacturer
Security Affairs
JANUARY 26, 2023
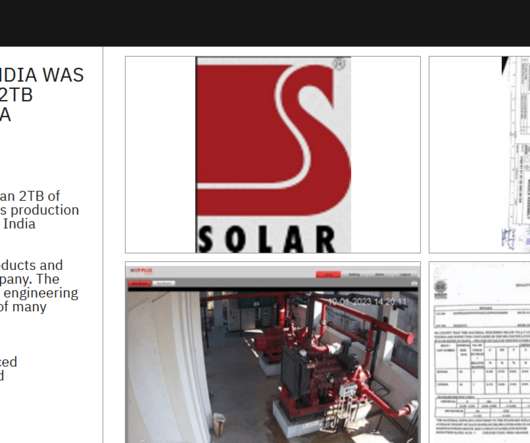
The BlackCat Ransomware group claims to have hacked SOLAR INDUSTRIES INDIA and to have stolen 2TB of “secret military data.” The BlackCat Ransomware group claims to have breached the company infrastructure and to have stolen 2TB of data, including secret military data related to weapons production.












































Let's personalize your content