How to Create & Implement a Cloud Security Policy
eSecurity Planet
SEPTEMBER 16, 2024
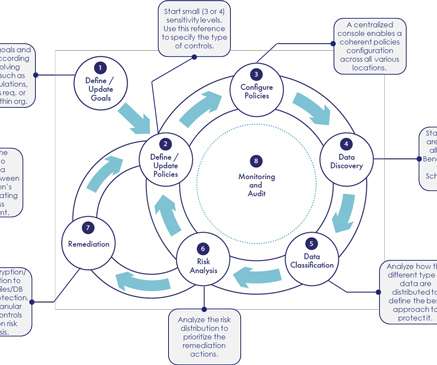
A cloud security policy is a comprehensive document that describes the organization’s guidelines for protecting cloud services. It specifies how data should be secured, who can access it, and the procedures for monitoring permissions. It establishes rules for cloud data security , access management, and threat response.












































Let's personalize your content