A Closer Look at the Snatch Data Ransom Group
Krebs on Security
SEPTEMBER 30, 2023
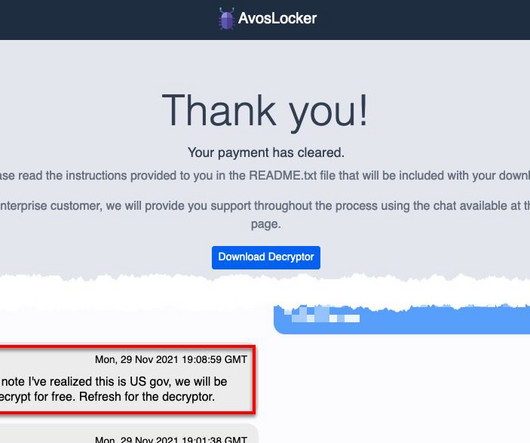
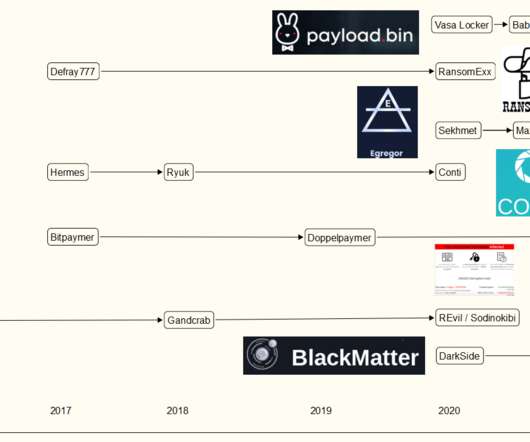
Earlier this week, KrebsOnSecurity revealed that the darknet website for the Snatch ransomware group was leaking data about its users and the crime gang’s internal operations. It continues: “Prior to deploying the ransomware, Snatch threat actors were observed spending up to three months on a victim’s system.











































Let's personalize your content