Swiss Air Force sensitive files stolen in the hack of Ultra Intelligence & Communications
Security Affairs
JANUARY 8, 2024
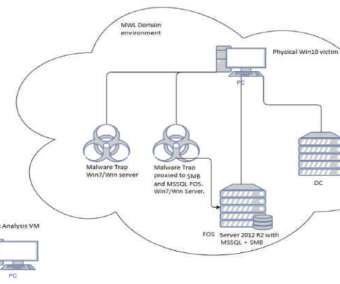
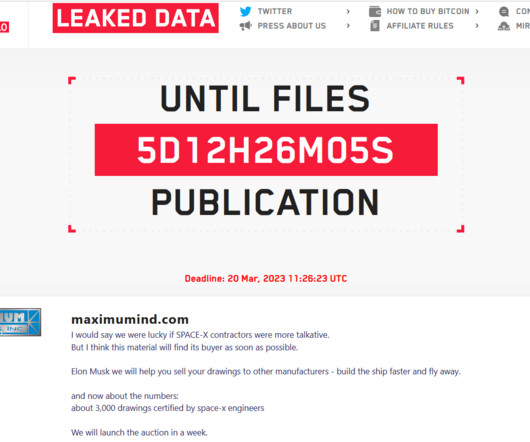
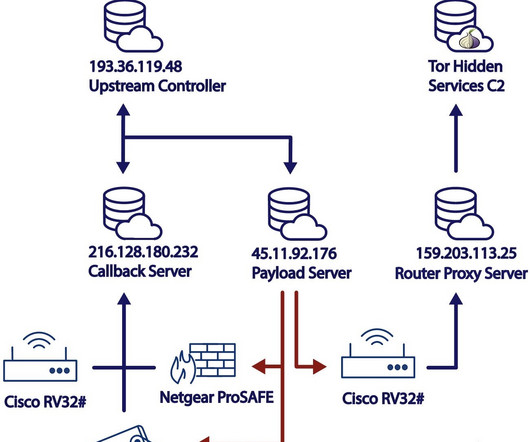
Documents belonging to the Swiss Air Force were leaked on the dark web as a result of cyberattack on a US security provider. Documents belonging to the Swiss Air Force were leaked on the dark web after the US security company Ultra Intelligence & Communications suffered a data breach. ” reported the SwissInfo website.



































Let's personalize your content