Threat Group TeamTNT Returns with New Cloud Attacks
eSecurity Planet
SEPTEMBER 21, 2022
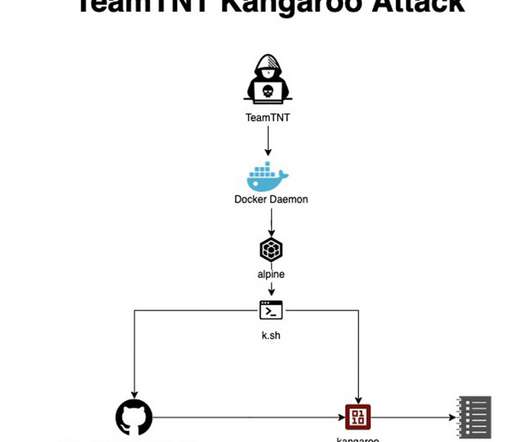
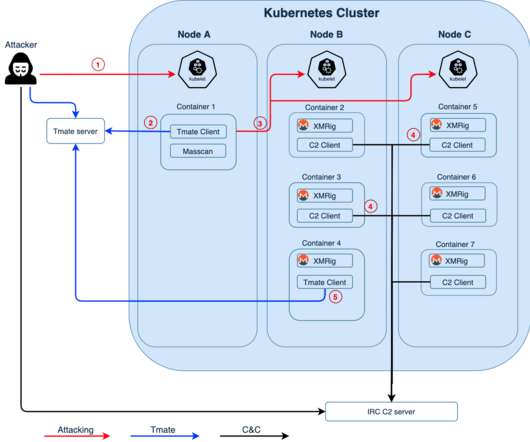
A retired threat actor has returned with new attacks aimed at the cloud, containers – and encryption keys. These cybercriminals are known for their creativity and ability to target cloud environments, as they introduced new techniques in 2020 that hadn’t been seen before. How to Protect Against Cloud, Container Threats.














































Let's personalize your content