Cryptohack Roundup: First Conviction in Smart Contract Hack
Data Breach Today
APRIL 18, 2024
Million of Cloud Services to Mine $1M of Crypto Every week, ISMG rounds up cybersecurity incidents in digital assets. Also: Nebraska Man Steals $3.5
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Data Breach Today
APRIL 18, 2024
Million of Cloud Services to Mine $1M of Crypto Every week, ISMG rounds up cybersecurity incidents in digital assets. Also: Nebraska Man Steals $3.5

Data Breach Today
JANUARY 21, 2023
Crypto Mining Campaign Targets Public Cloud Environments, Increases Security Risks Cybersecurity researchers say a Chinese for-profit threat group tracked as 8220 Gang is targeting cloud providers and poorly secured applications with a custom-built crypto miner and IRC bot.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 20, 2018
Don’t look now but cryptojacking may be about to metastasize into the scourge of cloud services. You can mine them, if you have a powerful CPU. Or you can hijack other people’s computers to do the mining. LW: I can’t really use my MacBook to mine Bitcoin, can I? LW: Somehow cryptojacking arose out of this?
Security Affairs
SEPTEMBER 22, 2022
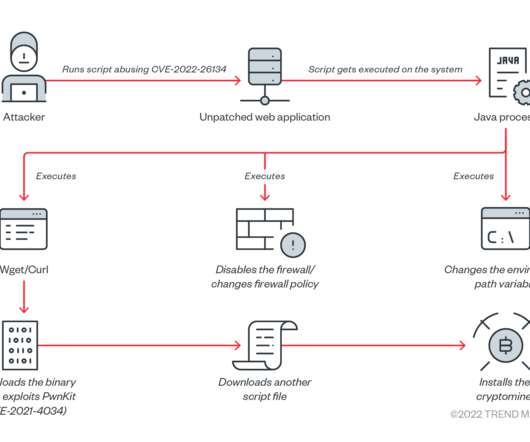
Threat actors are targeting unpatched Atlassian Confluence servers as part of an ongoing crypto mining campaign. Trend Micro researchers warn of an ongoing crypto mining campaign targeting Atlassian Confluence servers affected by the CVE-2022-26134 vulnerability. The gap is being abused for malicious cryptocurrency mining.”

Data Breach Today
JUNE 6, 2022
Cysiv's Cloud-Native Data Analytics Will Help OT and IoT Customers Address Threats Forescout has agreed to purchase startup Cysiv to help OT and IoT customers analyze, detect and respond to threats using cloud-native data analytics.

IBM Big Data Hub
AUGUST 28, 2023
One of the best ways to take advantage of social media data is to implement text-mining programs that streamline the process. What is text mining? When used strategically, text-mining tools can transform raw data into real business intelligence , giving companies a competitive edge. How does text mining work?
Krebs on Security
JANUARY 6, 2022
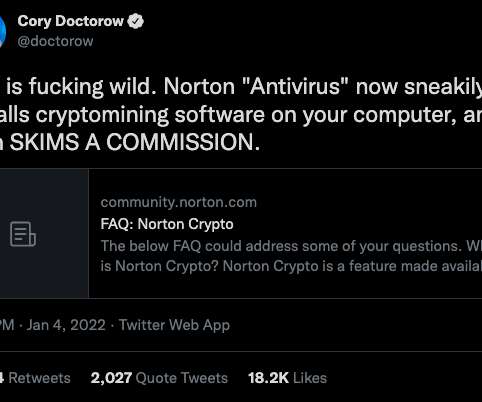
Norton 360 , one of the most popular antivirus products on the market today, has installed a cryptocurrency mining program on its customers’ computers. According to the FAQ posted on its site , “ Norton Crypto ” will mine Ethereum (ETH) cryptocurrency while the customer’s computer is idle. ” reads a Dec.

The Last Watchdog
AUGUST 3, 2018
Illicit crypto mining is advancing apace. It began when threat actors began stealthily embedding crypto mining functionality into the web browsers of unwitting individuals. Related article: Illicit crypto mining hits cloud services. Arsene: It’s important to understand that crypto mining may seem benign.

Security Affairs
JANUARY 14, 2024
million) worth of cryptocurrencies via mining activities. “The arrest comes after months of intensive collaboration between Ukrainian authorities, Europol and a cloud provider, who worked tirelessly to identify and locate the individual behind the widespread cryptojacking operation.” million) in cryptocurrencies.”

Security Affairs
SEPTEMBER 22, 2018
Additionally, the campaign is sophisticated in seeking to detect, analyse and neutralise other competing crypto-mining malware. I’ve been following the Monero mining pool address used in the Ngrok campaign and regularly checking for other research references on the internet. Introduction.
Security Affairs
DECEMBER 21, 2021
Researchers spotted a new botnet named Abcbot hat that mainly targeted Chinese cloud hosting providers over the past months. Security researchers discovered a new botnet, named Abcbot , that focused on Chinese cloud hosting providers over the past months. Follow me on Twitter: @securityaffairs and Facebook. Pierluigi Paganini.

eSecurity Planet
SEPTEMBER 21, 2022
A retired threat actor has returned with new attacks aimed at the cloud, containers – and encryption keys. These cybercriminals are known for their creativity and ability to target cloud environments, as they introduced new techniques in 2020 that hadn’t been seen before. How to Protect Against Cloud, Container Threats.
Security Affairs
MARCH 30, 2023
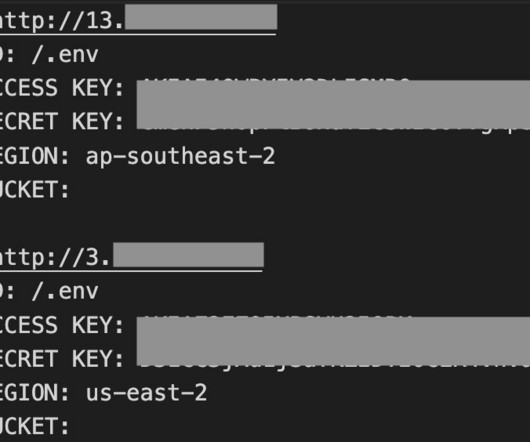
AlienFox is a novel comprehensive toolset for harvesting credentials for multiple cloud service providers, SentinelLabs reported. AlienFox is a new modular toolkit that allows threat actors to harvest credentials for multiple cloud service providers. ” concludes the report.

Security Affairs
MAY 12, 2019
Two hacking groups associated with large-scale crypto mining campaigns, Pacha Group and Rocke Group , wage war to compromise as much as possible cloud-based infrastructure. org is in this blacklist and it is known that Rocke Group has used this domain for their crypto-mining operations. “As an example, systemten[.]org

Data Breach Today
OCTOBER 11, 2019
Prosecutors Say Suspect Stole IDs and Cloud Resources to Mine Virtual Currencies A Singapore man allegedly ran a large-scale cryptocurrency mining scheme that involved using stolen identities to access Amazon and Google cloud computing resources, according to a 14-count U.S. Justice Department indictment.
Security Affairs
FEBRUARY 18, 2021
PaloAlto Network warns of the WatchDog botnet that uses exploits to take over Windows and Linux servers and mine cryptocurrency. 27, 2019 and already mined at least 209 Monero (XMR), valued to be around $32,056 USD. While there is currently no indication of additional cloud compromising activity at present (i.e.

Security Affairs
FEBRUARY 21, 2024
A new malware campaign targets Redis servers to deploy the mining crypto miner Migo on compromised Linux hosts. Caro Security researchers have observed a new malware campaign targeting Redis servers with a crypto miner dubbed Migo. The campaign stands out for the use of several novel system weakening techniques against the data store itself.

Data Breach Today
AUGUST 29, 2019
Thompson charges her with stealing 100 million records from Capital One, stealing data from at least 29 other organizations, as well as using hacked cloud computing servers to mine for cryptocurrency.

The Last Watchdog
SEPTEMBER 21, 2018
It’s rise in popularity has helped drive a new trend for start-ups to go “Cloud Native,” erecting their entire infrastructure, from the ground up, leveraging cloud services like Amazon Web Services, Microsoft Azure and Google Cloud. Security burden. Rising API exposures are another big security concern, by the way.

Threatpost
MARCH 30, 2021
Publicly available cloud images are spreading Monero-mining malware to unsuspecting cloud developers.

WIRED Threat Level
FEBRUARY 20, 2018
The recent rash of cryptojacking attacks has hit a Tesla database that contained potentially sensitive information.
Security Affairs
DECEMBER 12, 2022
Researchers spotted a cryptocurrency mining campaign targeting Linux users with Go-based CHAOS malware (Trojan.Linux.CHAOSRAT). In November 2022, Trend Micro researchers discovered a cryptocurrency mining campaign targeting Linux users with Go-based CHAOS malware (Trojan.Linux.CHAOSRAT).

Threatpost
APRIL 3, 2020
A Bitcoin-mining campaign using the Kinsing malware is spreading quickly thanks to cloud-container misconfigurations.

Dark Reading
SEPTEMBER 29, 2022
Cloud-native threats are costing cloud customer victims money as cryptojackers mine their vulnerable cloud instances.

IT Governance
MARCH 29, 2022
Perhaps the most significant example of this is the Cloud. public Clouds and 2.7 Millions of people rely on the Cloud to access information and services, with facilities filled with high-powered CPUs, terabytes of RAM and petabytes of storage. Then there’s blockchain mining. private ones. ISO 50001 and smarter energy use.
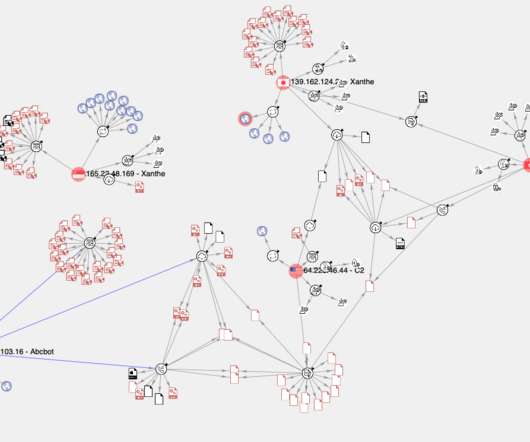
Security Affairs
JANUARY 10, 2022
Experts linked the C2 infrastructure behind an the Abcbot botnet to a cryptocurrency-mining botnet attack that was uncovered in December 2020. Experts linked the infrastructure used by the Abcbot DDoS botnet to the operations of a cryptocurrency-mining botnet that was uncovered in December 2020.

Security Affairs
OCTOBER 4, 2023
” According to the advisory, the vulnerability doesn’t impact Atlassian Cloud sites. Trend Micro researchers warned of a crypto mining campaign targeting Atlassian Confluence servers affected by the CVE-2022-26134 RCE vulnerability disclosed in early June 2022.

IBM Big Data Hub
APRIL 20, 2023
All are transforming their procurement operations by leveraging state-of-the-art process mining and intelligent automation technology. A Process Mining exercise drawing data from enterprise SAP has helped measure KPI performance and define the transformation roadmap. dollars annually in direct or indirect procurement.

Security Affairs
NOVEMBER 4, 2023
Kinsing threat actors are exploiting the recently disclosed Linux privilege escalation flaw Looney Tunables to target cloud environments. Researchers are cloud security firm Aqua have observed threat actors exploiting the recently disclosed Linux privilege escalation flaw Looney Tunables in attacks against cloud environments.

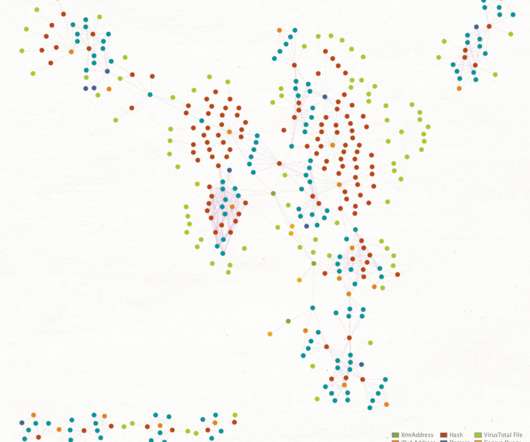
Security Affairs
MARCH 30, 2021
The expert determined the number of cryptocurrencies that were mined to a mining pool account by inspecting the mining pool. Half of the images discovered by the expert were using a shared mining pool, by he estimated that threat actors mined US$200,000 worth of cryptocurrencies in a two-year period.
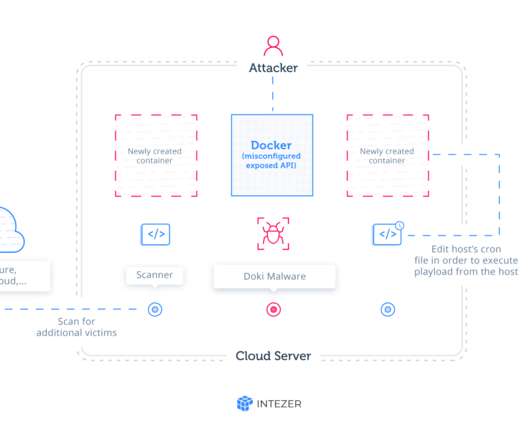
Security Affairs
JULY 29, 2020
The ongoing Ngrok mining botnet campaign is targeting servers are hosted on popular cloud platforms, including Alibaba Cloud, Azure, and AWS. “ Ngrok Mining Botnet is an active campaign targeting exposed Docker servers in AWS, Azure, and other cloud platforms. It has been active for at least two years.”

Dark Reading
JULY 7, 2021
Researchers discover more than 170 Android apps that advertise cloud cryptocurrency mining services and fail to deliver.
Threatpost
DECEMBER 11, 2020
The malware takes aim at PostgreSQL database servers with never-before-seen techniques.
Security Affairs
SEPTEMBER 9, 2021
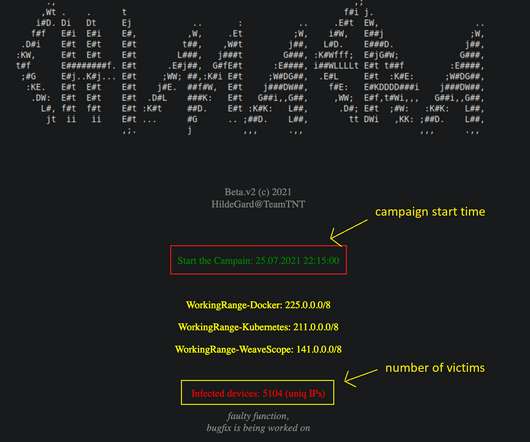
The TeamTNT botnet is a crypto-mining malware operation that has been active since April 2020 and that targets Docker installs. Researchers from Palo Alto Networks, that analyzed the same campaign , reported that the group is also using a cloud penetration testing toolset to target cloud-based apps that is named Peirates.
Security Affairs
NOVEMBER 10, 2023
Threat actors relied on access to multiple virtual private servers (VPS) in conjunction with rented cloud infrastructure, open proxies, and DDoS tools. In early June, Microsoft suffered severe outages for some of its services, including Outlook email, OneDrive file-sharing apps, and the cloud computing infrastructure Azure.

Security Affairs
NOVEMBER 22, 2023
Researchers from Aqua Nautilus spotted experimental incursions into cloud environments by Kinsing actors. Intriguingly, the attacker is also broadening the horizons of their cloud-native attacks by extracting credentials from the Cloud Service Provider (CSP).” reads the analysis published by Aqua firm.

Security Affairs
APRIL 22, 2022
The Lemon_Duck cryptomining botnet is targeting Docker servers to mine cryptocurrency on Linux systems. Crowdstrikes researchers reported that the Lemon_Duck cryptomining botnet is targeting Docker to mine cryptocurrency on Linux systems. “The “a.asp” file is the actual payload in this attack. Kills known network connections.

ForAllSecure
APRIL 4, 2023
Incident response in the cloud. James Campbell, CEO of Cado Security , shares his experience with traditional incident response, and how the cloud, with its elastic structure, able to spin up and spin down instances, is changing incident response. That's the unique thing about clouds that's a different challenge.

OpenText Information Management
NOVEMBER 24, 2021
The latest announcement by OpenText of Cloud Editions includes some great updates to OpenText™ Decisiv™. Integrate Decisiv with OpenText™ Magellan™ Text Mining for enhanced document filtering capabilities Find relevant content faster with?AI-assisted AI-assisted Magellan text mining capabilities.

Daymark
APRIL 6, 2021
Cloud security is a constant concern for organizations of every size. The malicious actor located in Moscow who obtains this userID (likely an email of mine) and password then does a quick lookup on LinkedIn and finds that I work at Daymark. One area of particular concern is legitimately compromised user credentials.
OpenText Information Management
APRIL 8, 2020
The current global pandemic is bringing new significance to the word “disruptive,” bringing extreme levels of uncertainty and testing the leadership and response of companies, public sector organizations and the … The post Announcing OpenText AI & Analytics Cloud Editions (CE) 20.2 appeared first on OpenText Blogs.
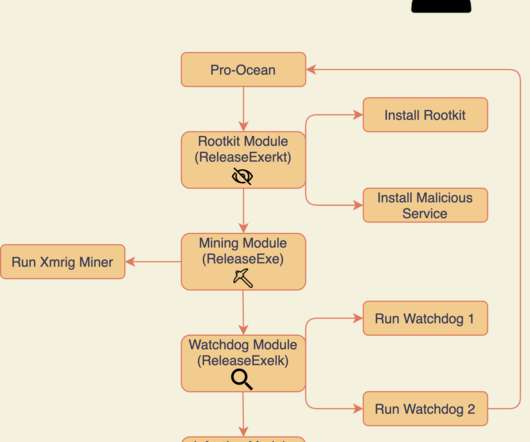
Security Affairs
JANUARY 31, 2021
The new malware implement new and improved rootkit and worm capabilities, it continues to target cloud applications by exploiting known vulnerabilities such as Oracle WebLogic ( CVE-2017-10271 ) and Apache ActiveMQ ( CVE-2016-3088 ) servers. “Pro-Ocean uses known vulnerabilities to target cloud applications.
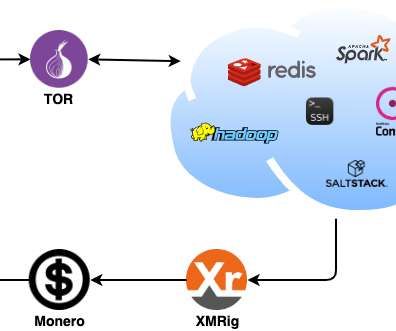
Security Affairs
JANUARY 25, 2021
. “These techniques include numerous modules that exploit implicit trust, weak passwords, and unauthenticated remote code execution (RCE) vulnerabilities in popular applications, including Secure Shell (SSH), IT administration tools, a variety of cloud-based applications, and databases.” Ransomware, data theft).

Security Affairs
MAY 26, 2021
. “Most of the compromised nodes were from China and the US identified in the ISP (Internet Service Provider) list, which had Chinese and US-based providers as the highest hits, including some CSPs (Cloud Service Providers).” The malware deploys the XMRig mining tool to mine Monero cryptocurrency. Pierluigi Paganini.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content