Mastermind behind 1.8 million cryptojacking scheme arrested in Ukraine
Security Affairs
JANUARY 14, 2024
million) worth of cryptocurrencies via mining activities. “The arrest comes after months of intensive collaboration between Ukrainian authorities, Europol and a cloud provider, who worked tirelessly to identify and locate the individual behind the widespread cryptojacking operation.” million) in cryptocurrencies.”





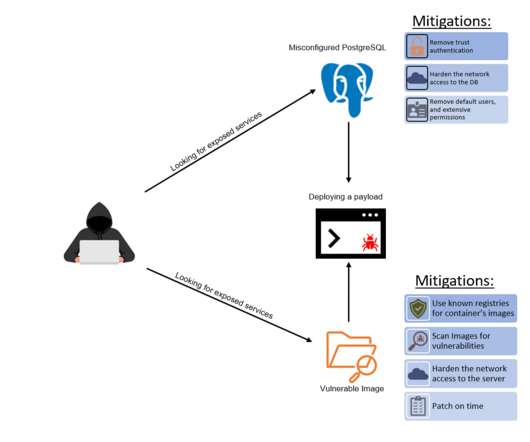


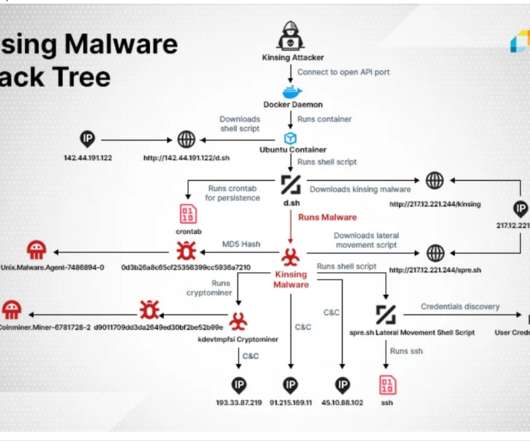



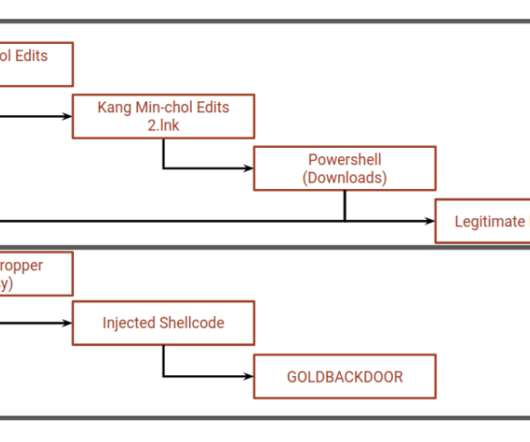

































Let's personalize your content