Resecurity Released a Status Report on Drug Trafficking in the Dark Web (2022-2023)
Security Affairs
JANUARY 9, 2023
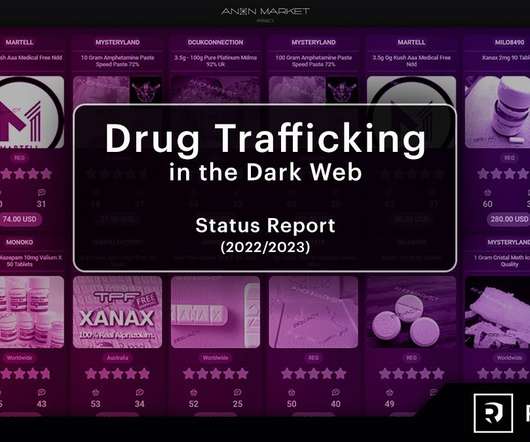
The Resecurity® Hunter unit performed an extensive analysis of current trends and dynamics related to the underground economy around active DNMs leveraging technical means and human intelligence (HUMINT) sources. Resecurity noticed a sharp increase in demand for prescription pharmaceuticals.

























Let's personalize your content