New Hive ransomware variant is written in Rust and use improved encryption method
Security Affairs
JULY 6, 2022
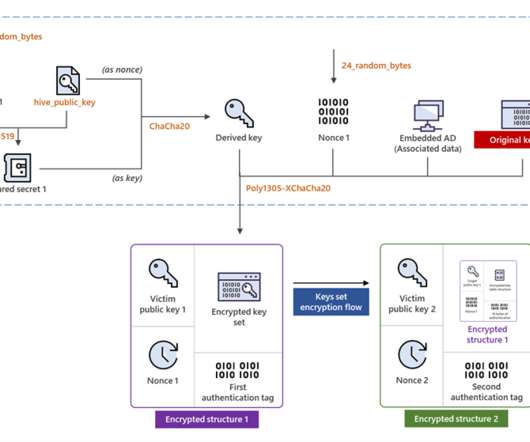
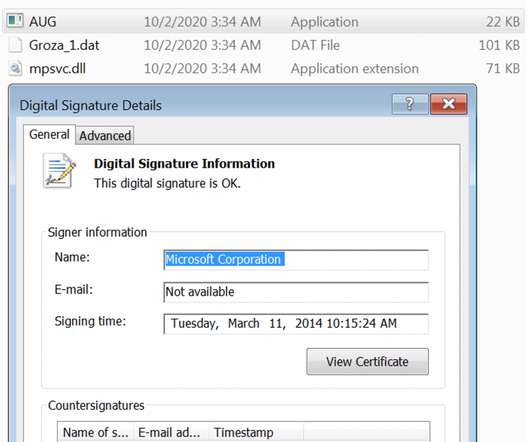
Hive ransomware operators have improved their file-encrypting module by migrating to Rust language and adopting a more sophisticated encryption method. The most important change in the latest Hive variant is the encryption mechanism it adopts. ” reads the post published by Microsoft. ” continues Microsoft. .







































Let's personalize your content