Croatia government agencies targeted with news SilentTrinity malware
Security Affairs
JULY 7, 2019
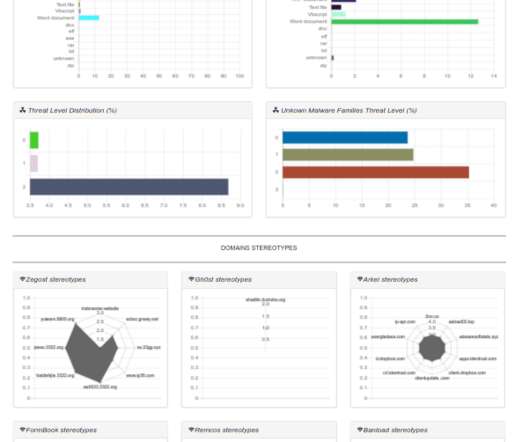
Croatia government agencies have been targeted by unknown hackers with a new piece of malware tracked as SilentTrinity. A mysterious group of hackers carried out a series of cyber attacks against Croatian government agencies, infecting employees with a new piece of malware tracked as SilentTrinity. ” reads one of the alerts.




































Let's personalize your content