Russia-linked APT29 group exploited WinRAR 0day in attacks against embassies
Security Affairs
NOVEMBER 20, 2023
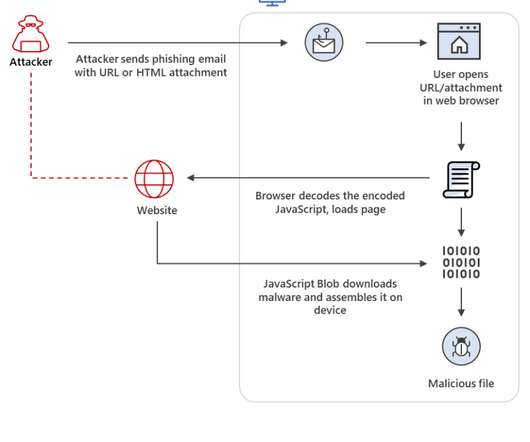
The Russia-linked APT group was observed using a specially crafted ZIP archive that runs a script in the background to show a PDF lure while downloading PowerShell code to fetch and execute a payload. Google TAG experts also observed the Russia-linked ATP28 group exploiting the flaw in attacks against Ukraine users.

















Let's personalize your content