Analysis: Third-Party Health Data Breaches Dominated in 2022
Data Breach Today
JANUARY 10, 2023
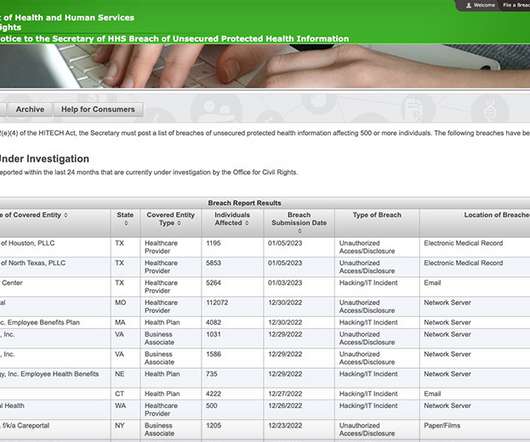
HHS Breach Tally Signals Biggest Risks, Threats Likely in 2023 Hacking and third-party business associate incidents were the crux of the largest health data breaches reported to federal regulators in 2022, foreshadowing the top risks and threats that will likely plague healthcare entities and their vendors in the new year, as well.





































Let's personalize your content