Google Exposes Initial Access Broker Ties to Ransomware
Data Breach Today
MARCH 19, 2022
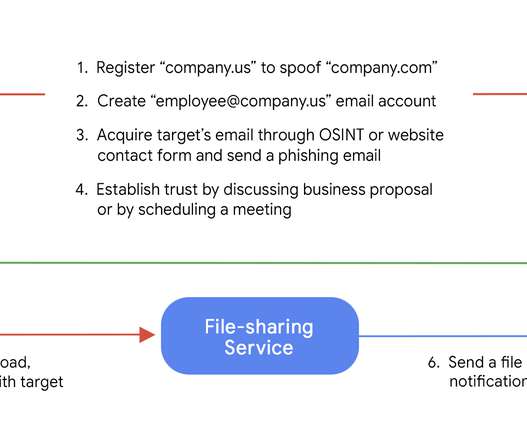
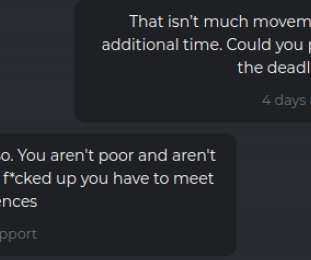
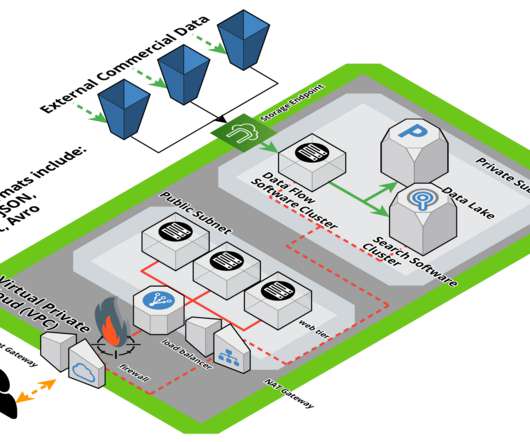
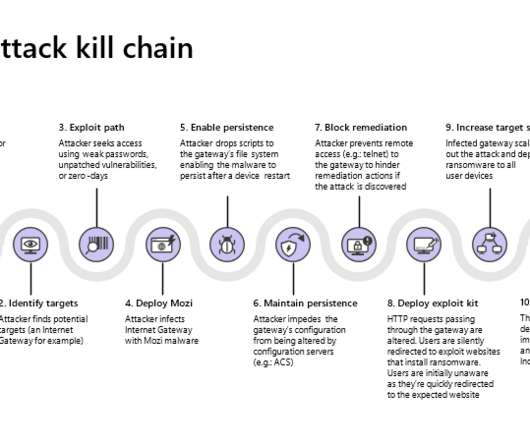
Broker Provides Services to Conti, Diavol Ransomware Groups Researchers have uncovered a full-time initial access broker group that serves both Conti and Diavol ransomware groups.









































Let's personalize your content