500M Avira Antivirus Users Introduced to Cryptomining
Krebs on Security
JANUARY 8, 2022
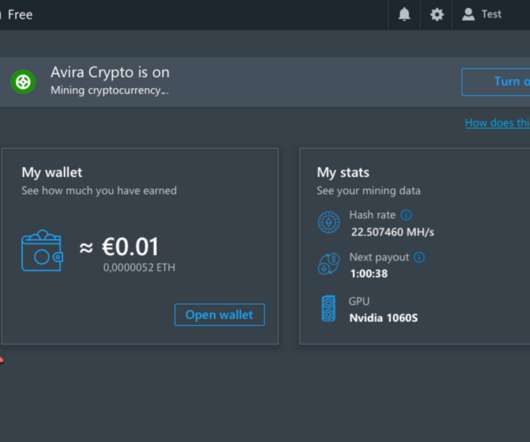
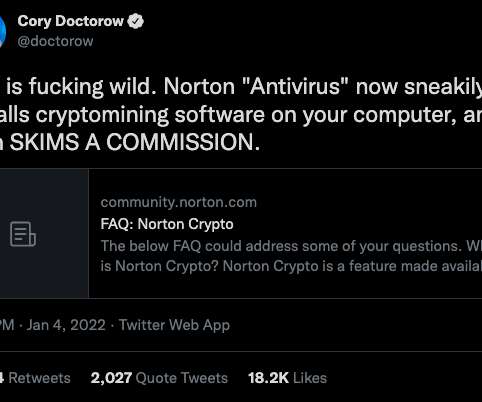
Many readers were surprised to learn recently that the popular Norton 360 antivirus suite now ships with a program which lets customers make money mining virtual currency. In 2017, the identity theft protection company LifeLock was acquired by Symantec Corp. Avira Free Antivirus). In January 2021, Avira was acquired by Tempe, Ariz.-based













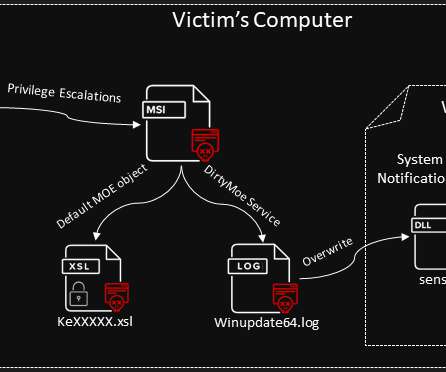

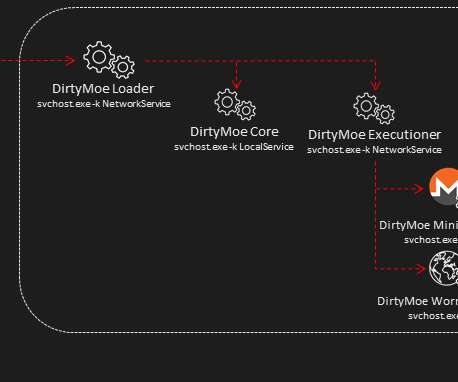


















Let's personalize your content