Chinese-Linked APT Spying On Organizations for 10 Years
Data Breach Today
JUNE 12, 2022
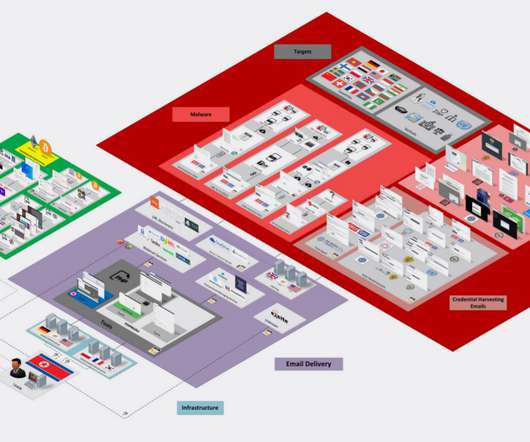
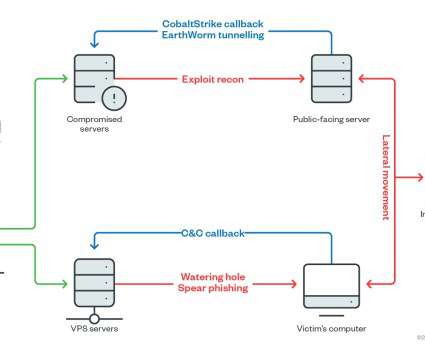
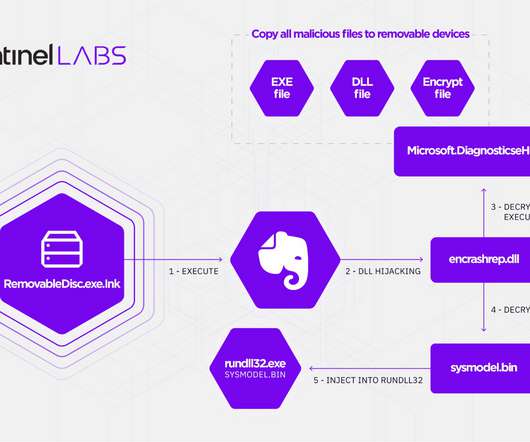
Attacker Use DLL hijacking, DNS tunneling to Evade Post-Compromise Detection A recently identified Chinese hacking group dubbed "Aoqin Dragon" has been found to have targeted government, education and telecommunication organizations in Southeast Asia and Australia since 2013 as part of an ongoing cyberespionage campaign, according to research from (..)










































Let's personalize your content