FTC Issues Notice of Proposed Rulemaking to Update COPPA Rule
Hunton Privacy
DECEMBER 22, 2023
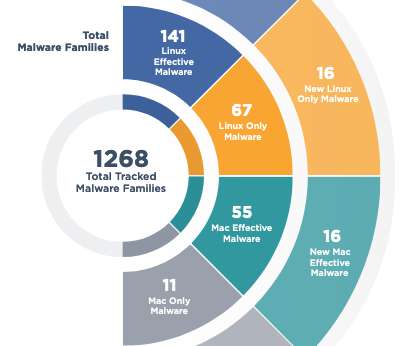
The COPPA Rule has not been updated since 2012. The use of education technology (“ed tech”) would be limited and the changes would codify guidance that bars students’ personal information being used for commercial purposes. Strengthening data security. Restricting ed tech in schools.



























Let's personalize your content