Who Stole 3.6M Tax Records from South Carolina?
Krebs on Security
APRIL 16, 2024
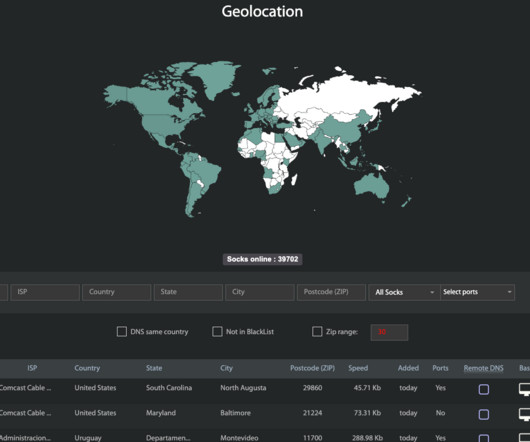
The answer may no longer be a mystery: KrebsOnSecurity found compelling clues suggesting the intrusion was carried out by the same Russian hacking crew that stole of millions of payment card records from big box retailers like Home Depot and Target in the years that followed. Nikki Haley to head the state’s law enforcement division.






































Let's personalize your content