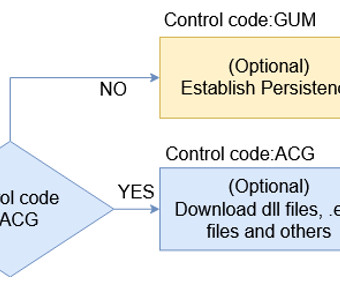
Russia-linked APT28 used post-compromise tool GooseEgg to exploit CVE-2022-38028 Windows flaw
Security Affairs
APRIL 22, 2024
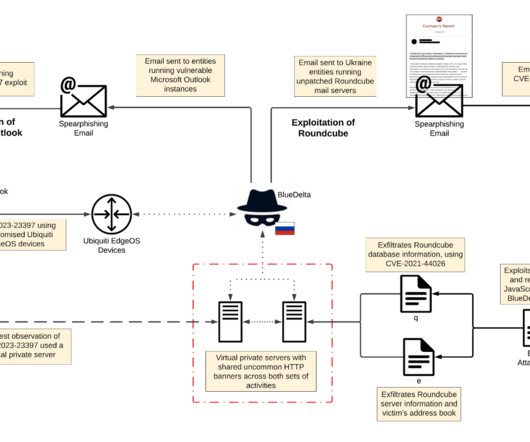
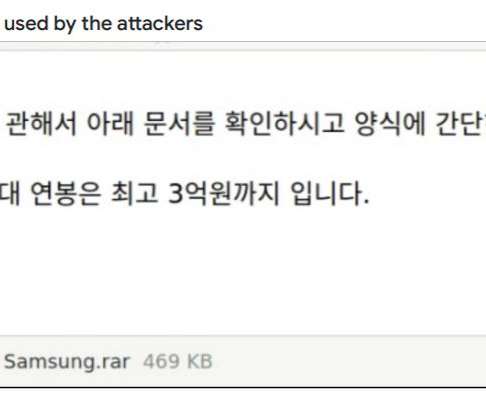
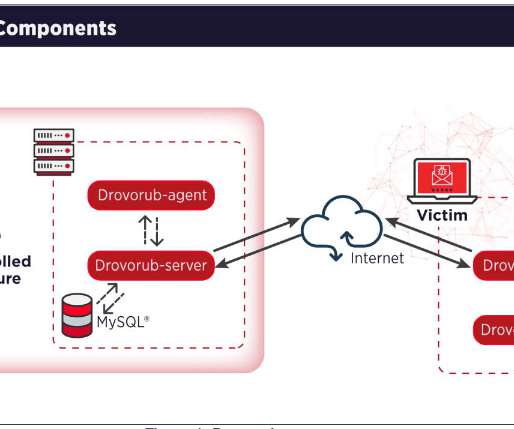
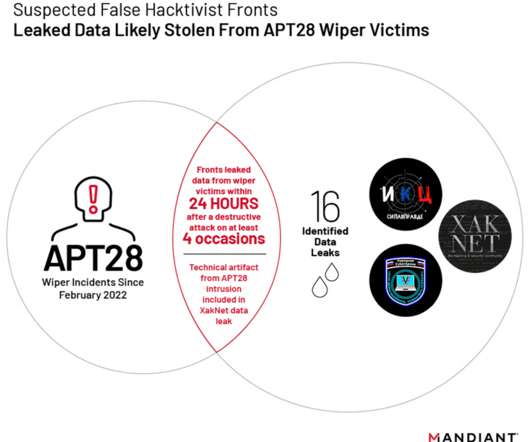
The APT28 group (aka Forest Blizzard , Fancy Bear , Pawn Storm , Sofacy Group , Sednit , BlueDelta, and STRONTIUM ) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. Most of the APT28s’ campaigns leveraged spear-phishing and malware-based attacks.





























Let's personalize your content