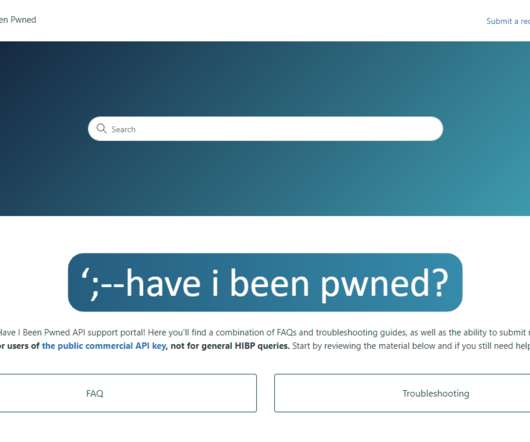
Better Supporting the Have I Been Pwned API with Zendesk
Troy Hunt
NOVEMBER 3, 2022
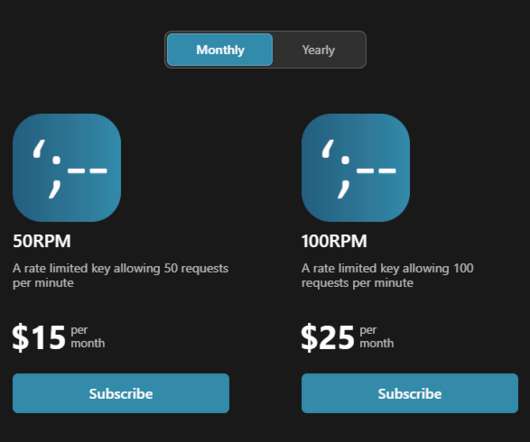
You could read the instructions when signing up for a key, but who remembers what they read months ago? There's also a greater expectation of support for everything from how to construct an API request to what to do when you keep getting 429 responses because you're (allegedly) making too many requests. I don't know!





















Let's personalize your content