Mozi infections will slightly decrease but it will stay alive for some time to come
Security Affairs
SEPTEMBER 1, 2021
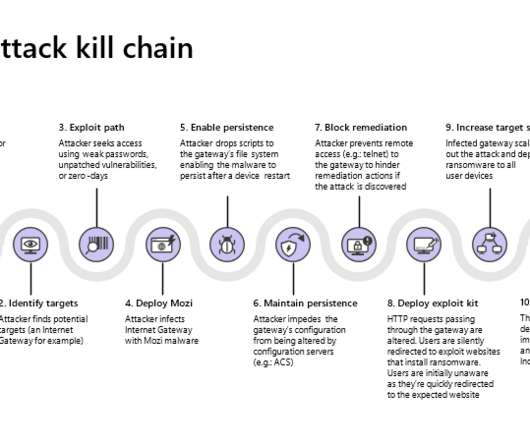
The bot spreads by brute-forcing devices online or by exploiting known unpatched vulnerabilities in the target devices. The capabilities to target Netgear, Huawei, and ZTE gateways allow the bot to increase its resistance to takedown. The mozi author has been arrested few weeks ago by LE with information provided by our team.



























Let's personalize your content