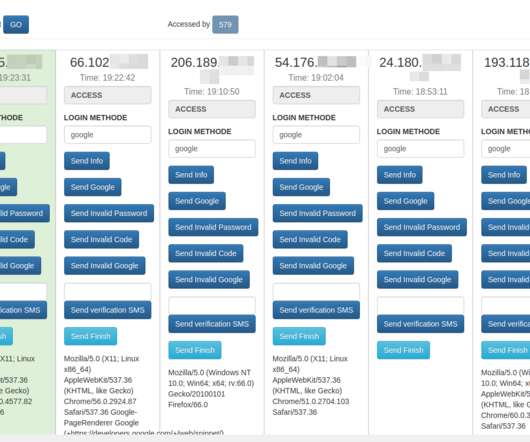
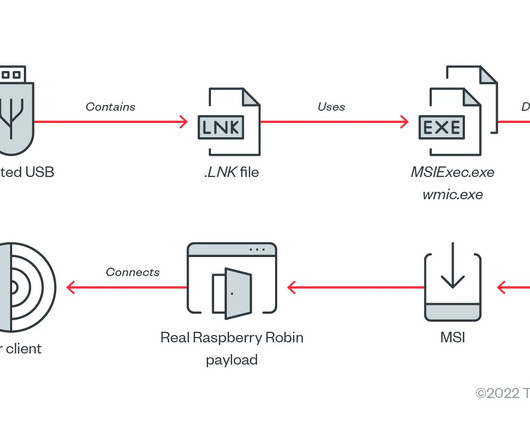
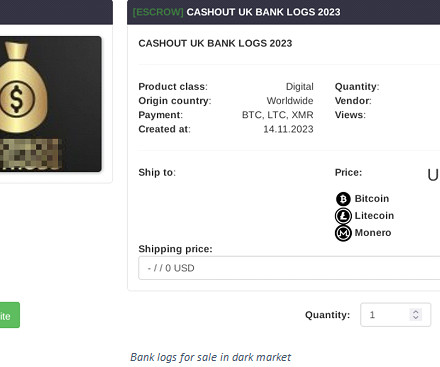
Phishing Remains the Most Common Attack Technique, With Malicious URL Use Increasing 144%
KnowBe4
DECEMBER 13, 2023
Analysis of nearly a year’s worth of emails brings insight into exactly what kinds of malicious content are being used, who’s being impersonated, and who’s being targeted.








































Let's personalize your content