Experian Glitch Exposing Credit Files Lasted 47 Days
Krebs on Security
JANUARY 25, 2023
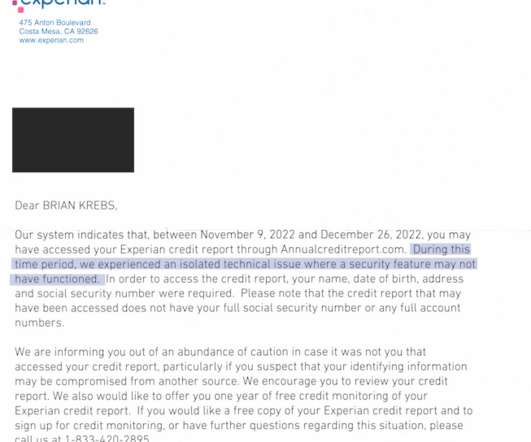
The tip about the Experian weakness came from Jenya Kushnir , a security researcher living in Ukraine who said he discovered the method being used by identity thieves after spending time on Telegram chat channels dedicated to cybercrime. . To make matters worse, a majority of the information in that credit report is not mine.


















Let's personalize your content