Shift happens: the future office/library in a connected world
CILIP
SEPTEMBER 21, 2021
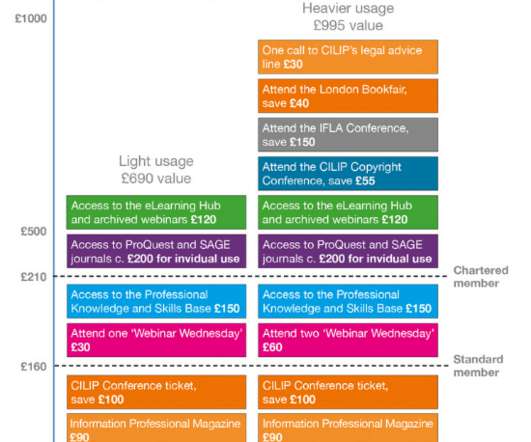
Shift happens: the future office/library in a connected world. Work happens anywhere where you may well be with the digital tools as your disposal. We have different social, digital tools that allow us to connect, learn, share and collaborate ? and, yes, the library. So what role can libraries play in the new normal ?







































Let's personalize your content