US Disrupts Russian Military Intelligence Botnet
Data Breach Today
FEBRUARY 15, 2024
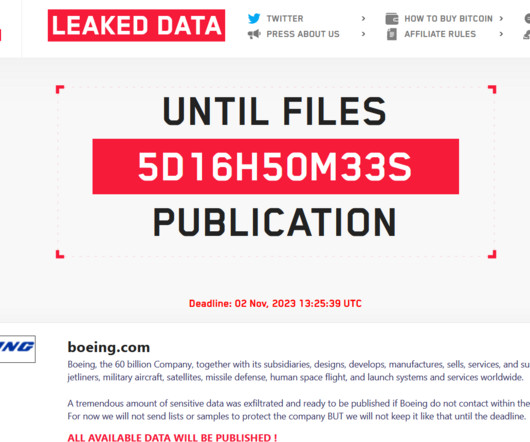
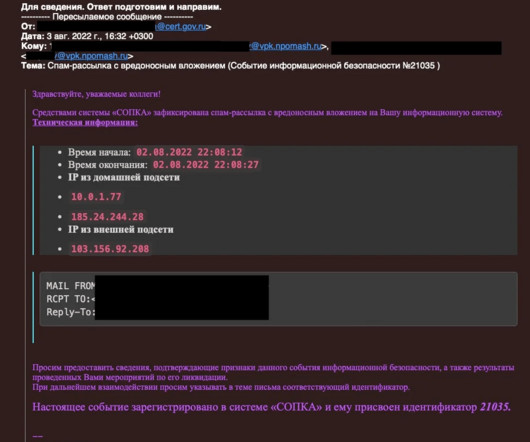
federal government says it disrupted a criminal botnet that Russian military intelligence had converted into a platform for global cyberespionage. The malware targets Linux-based IoT devices - in this case, routers made by New York manufacturer Ubiquiti. GRU Hackers Commandeered 'Moobot' for Cyberespionage The U.S.








































Let's personalize your content