Hackers Target Wind Turbine Manufacturer Nordex
Data Breach Today
APRIL 4, 2022
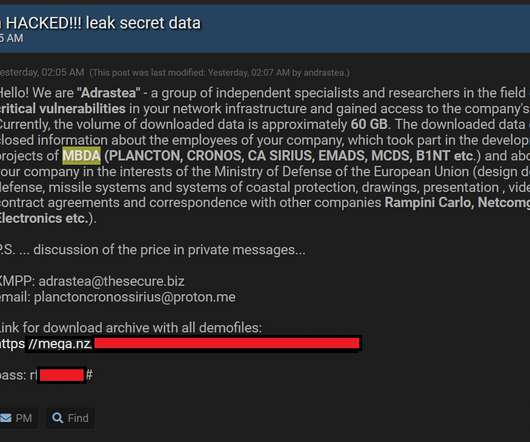
Company Initiates Complete Shutdown of IT Systems; Attack May Link to Viasat German wind turbine manufacturer Nordex, which develops, manufactures and distributes wind power systems across the world, has switched off its IT systems in multiple locations after a reported cybersecurity incident.











































Let's personalize your content