Cyber-insurance – 72 hours for the insured party to file a criminal complaint: GDPR’s false friend
Data Protection Report
MARCH 21, 2023
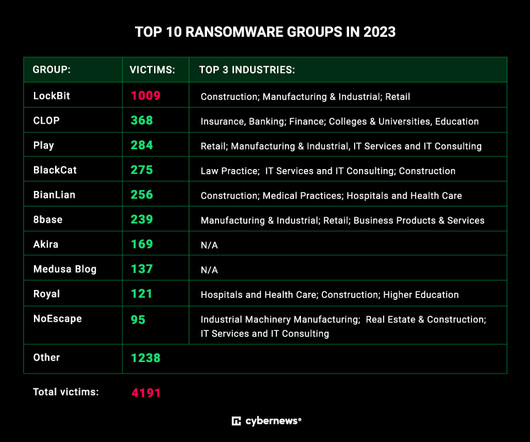
The French Information and Digital Security Experts Club ( CESIN ) has estimated that 54% of French companies were subject to cyberattacks in 2021, [1] while France Assureurs has put cyberattack risks on top of all other risks for the sixth year in a row. [2] 12-10-1 into the French Insurance code. However, in the end, Article L.12-10-1
















































Let's personalize your content