The surveys speak: supply chain threats are freaking people out
The Security Ledger
MAY 10, 2023
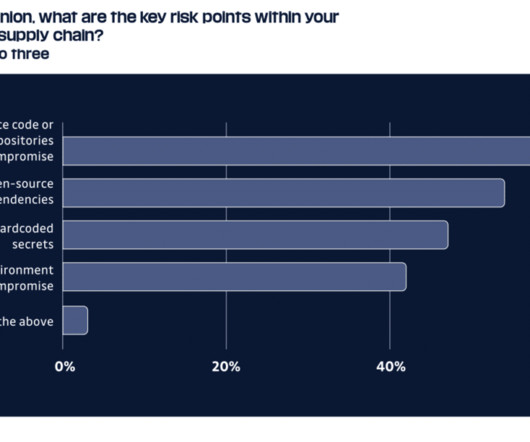
A bunch of recent surveys of IT and security pros send a clear message: threats and risks from vulnerable software supply chains are real, and they’re starting to freak people out. The post The surveys speak: supply chain threats are freaking people out appeared first on The Security Ledger with Paul F. Related Stories Forget the IoT.
















































Let's personalize your content