Google: China dominates government exploitation of zero-day vulnerabilities in 2023
Security Affairs
MARCH 28, 2024
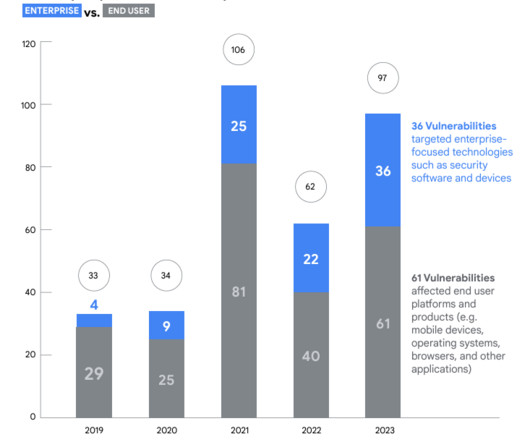
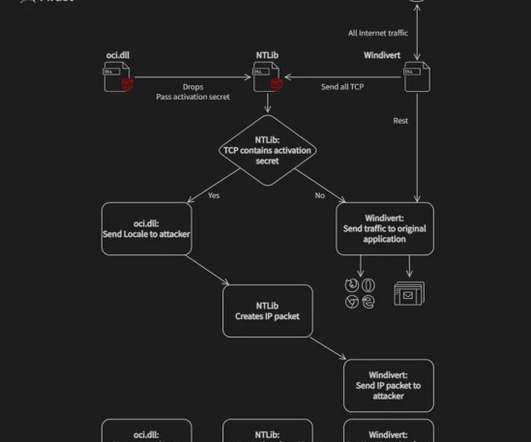
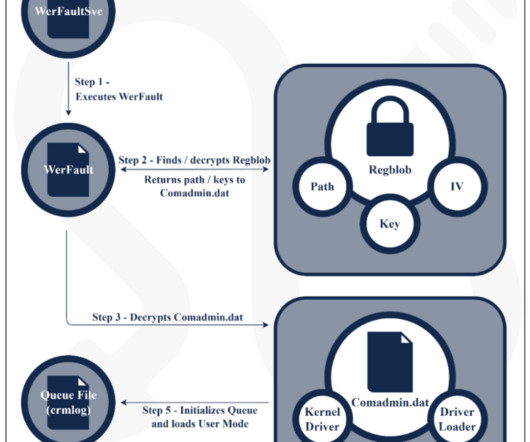
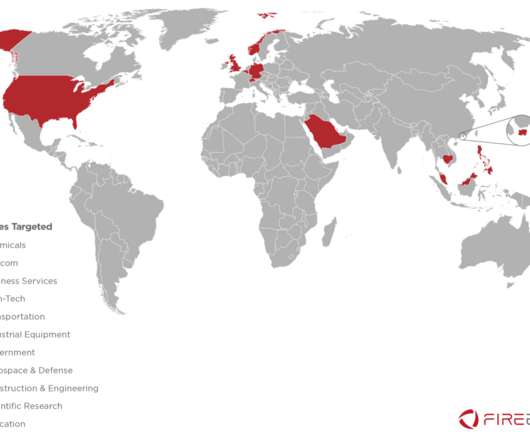
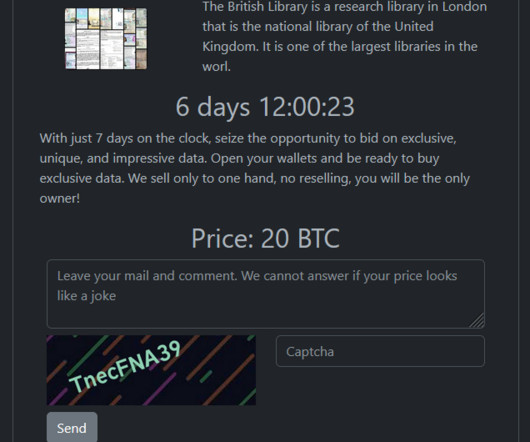
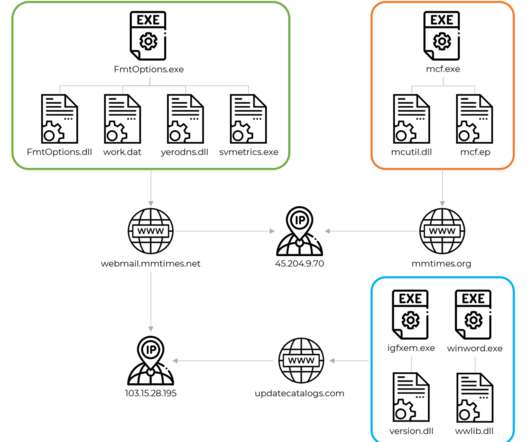
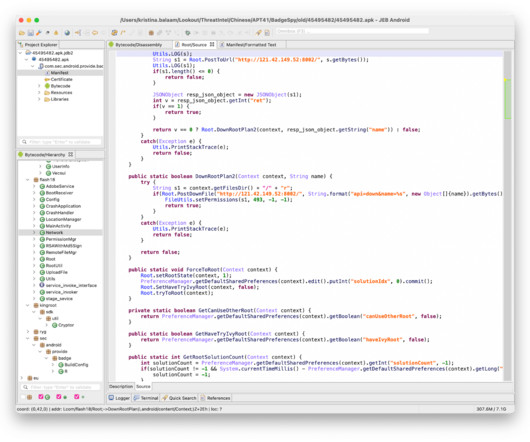
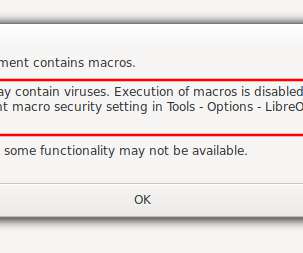
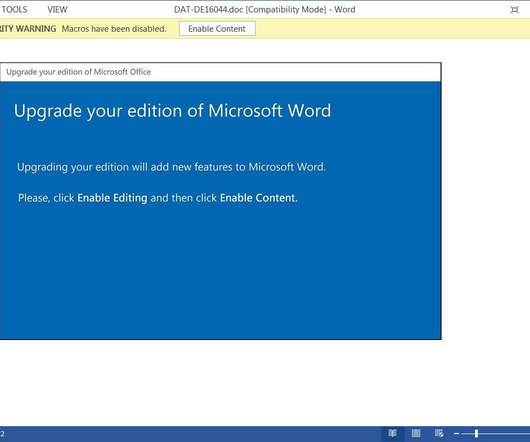
In 2023, the researchers observed a surge in zero-day vulnerabilities in third-party components and libraries that can impact all products that use them. The Chinese government made the headlines because government-linked APT groups exploited 12 zero-day vulnerabilities in 2023, which marks a notable increase from seven in 2022.



































Let's personalize your content