SYS01 stealer targets critical government infrastructure
Security Affairs
MARCH 7, 2023
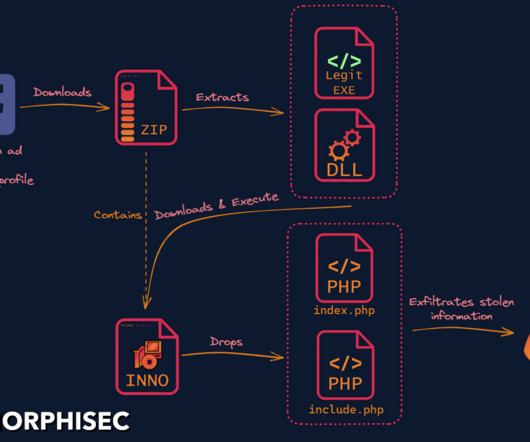
Researchers discovered a new info stealer dubbed SYS01 stealer targeting critical government infrastructure and manufacturing firms. ” reads the analysis published by Morphisec. to lure victims into downloading a malicious file. ” reads the analysis published by Morphisec.












































Let's personalize your content