Lionsgate streaming platform with 37m subscribers leaks user data
Security Affairs
MARCH 22, 2023
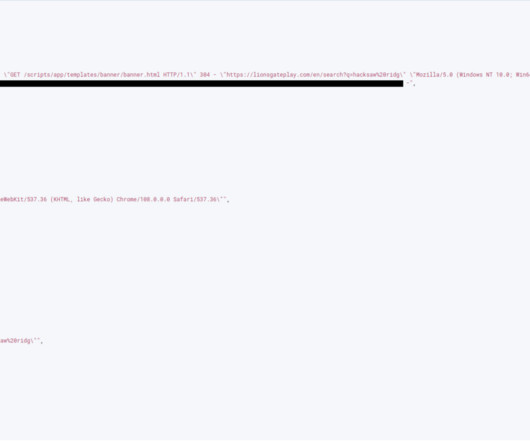
URLs found in logs contained titles and IDs of what content users watched on the platform, along with search queries entered by the users. The research by Cybernews is a stellar example of this tendency. Logs also leaked the platform’s usage data, typically used for analytics and performance tracking.




































Let's personalize your content