What is Tailgating? Definition, Examples & Prevention
IT Governance
JULY 27, 2023
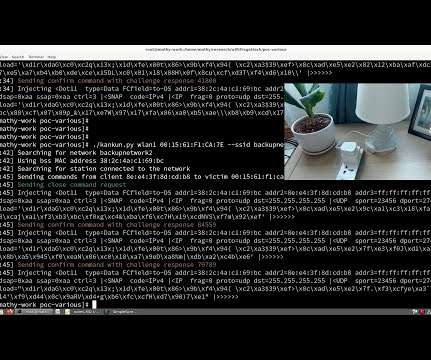
Fraudsters have countless tricks up their sleeves to bypass security measures and access sensitive information. The same principle, believe it or not, applies in a cyber security context. More specifically, the fraudster is trying to gain physical access to a secure part of the premises so that they can steal confidential information.














































Let's personalize your content