Thousands of Humana customers have their medical data leaked online by threat actors
Security Affairs
JULY 21, 2021
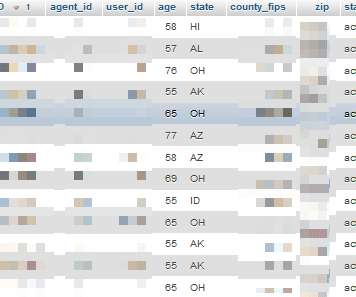
Experts found a DB containing sensitive health insurance data belonging to customers of US insurance giant Humana. An SQL database containing what appears to be highly sensitive health insurance data of more than 6,000 patients has been leaked on a popular hacker forum. What was leaked? Drug prescription listings).
























Let's personalize your content