Resecurity Released a Status Report on Drug Trafficking in the Dark Web (2022-2023)
Security Affairs
JANUARY 9, 2023
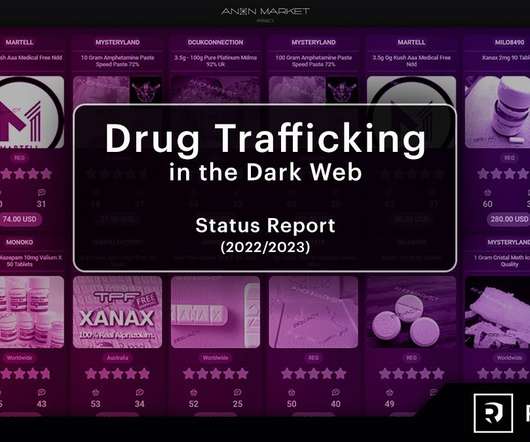
Resecurity detailed the increasing tensions between different influence groups behind illegal marketplaces in Dark Web – attacking each other, performing DDoS attacks and trying to abuse the reputation of competitors to capture a bigger market share. Resecurity noticed a sharp increase in demand for prescription pharmaceuticals.

































Let's personalize your content