Nation-State-Sponsored Attacks: Not Your Grandfather’s Cyber Attacks
Data Matters
MAY 17, 2022
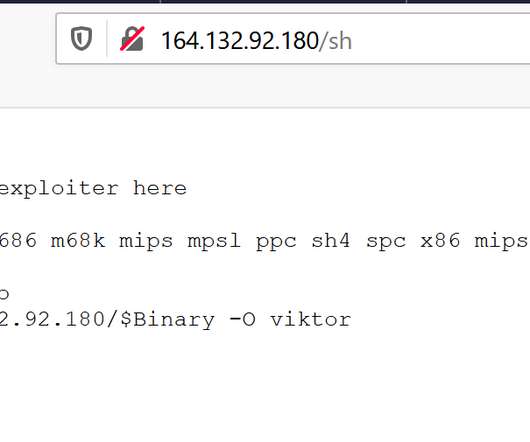
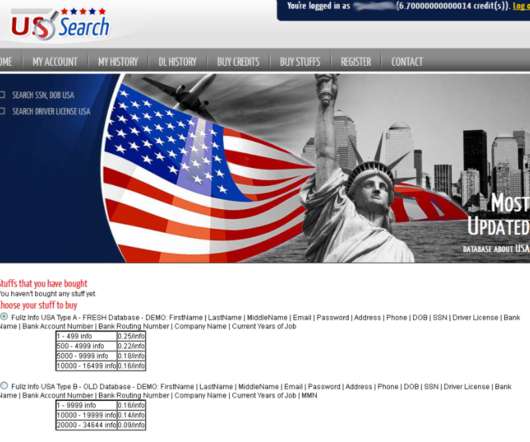
Attorney General described a recent takedown of a Russian government-sponsored botnet called Cyclops Blink before it was weaponized and caused damage. and foreign government agencies. government reported a significant rise in hacks perpetrated against private companies by nation-state-sponsored threat actors. Agency (Feb.


























Let's personalize your content