Thales collaborates with Hewlett Packard Enterprise to Enhance 5G Subscriber Privacy and Security
Thales Cloud Protection & Licensing
DECEMBER 21, 2022
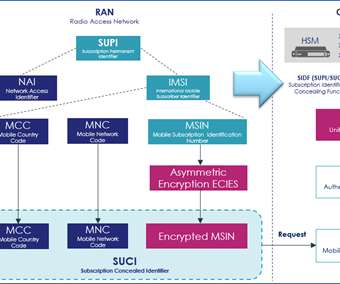
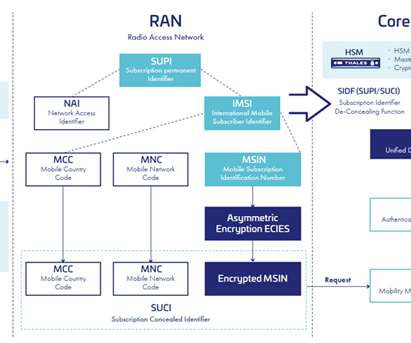
Thales collaborates with Hewlett Packard Enterprise to Enhance 5G Subscriber Privacy and Security. Thales collaborates with Hewlett Packard Enterprise (HPE) to provide enhanced privacy and secure authentication for global 5G users, further extending its partner ecosystem. The challenge of 5G security and privacy.
















































Let's personalize your content