HackerGPT 2.0 Unveils New AI Cyber Defense Strategies
eSecurity Planet
MARCH 15, 2024
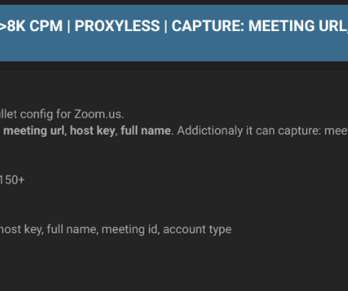
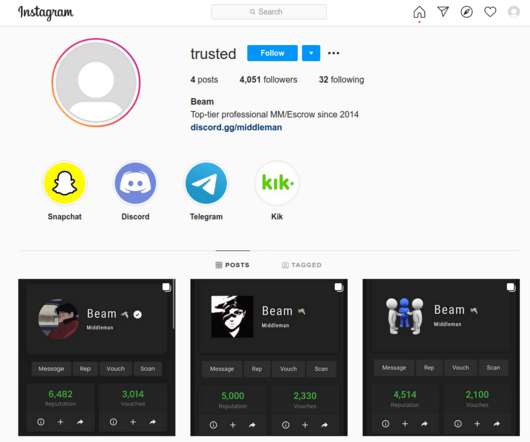
in February 2024, it serves as an extensive repository of hacking tools and techniques to actively assist users in managing complex cybersecurity protection strategies. From analyzing attack methods and suggesting defense tactics to doing vulnerability assessments, it provides users with the knowledge to improve their security posture.








































Let's personalize your content