China-linked APT41 group spotted using open-source red teaming tool GC2
Security Affairs
APRIL 17, 2023
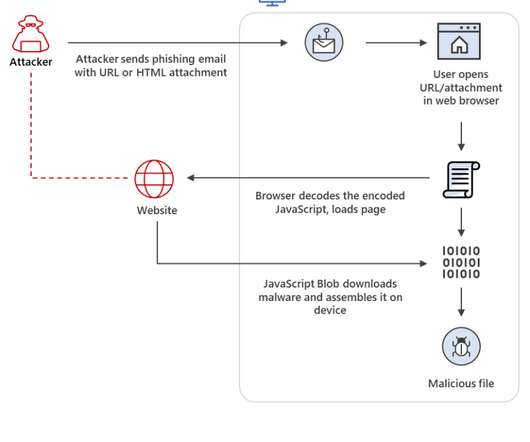
China-linked APT41 group used the open-source red teaming tool GC2 in an attack against a Taiwanese media organization. Google Threat Analysis Group (TAG) team reported that the China-linked APT41 group used the open-source red teaming tool Google Command and Control ( GC2 ) in an attack against an unnamed Taiwanese media organization.



























Let's personalize your content