10 Mistakes Companies Make in Their Ransomware Responses
Dark Reading
JULY 14, 2021
Hit by ransomware? These missteps can take a bad scenario and make it even worse

Dark Reading
JULY 14, 2021
Hit by ransomware? These missteps can take a bad scenario and make it even worse

Dark Reading
JULY 12, 2021
Microsoft Active Directory, ubiquitous across enterprises, has long been a primary target for attackers seeking network access and sensitive data.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

OpenText Information Management
JULY 12, 2021
According to EFT, 55 percent of supply chain executives considered web service APIs as an alternative to EDI. But we should know better by now than try to write off electronic data interchange (EDI) again. This isn’t about replacement. It is, as always, about integration.

Data Breach Today
JULY 16, 2021
Palo Alto Networks Report Describes Tactics of Group Leveraging Open-Source Tools The gang behind the ransomware strain known as Mespinoza, aka PYSA, is targeting manufacturers, schools and others, mainly in the U.S. and U.K., demanding ransom payments as high as $1.6 million, according to Palo Alto Networks' Unit 42, which says the group leverages open-source tools.

Advertisement
Generative AI is upending the way product developers & end-users alike are interacting with data. Despite the potential of AI, many are left with questions about the future of product development: How will AI impact my business and contribute to its success? What can product managers and developers expect in the future with the widespread adoption of AI?

Krebs on Security
JULY 13, 2021
Microsoft today released updates to patch at least 116 security holes in its Windows operating systems and related software. At least four of the vulnerabilities addressed today are under active attack, according to Microsoft. Thirteen of the security bugs quashed in this month’s release earned Microsoft’s most-dire “critical” rating, meaning they can be exploited by malware or miscreants to seize remote control over a vulnerable system without any help from users.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
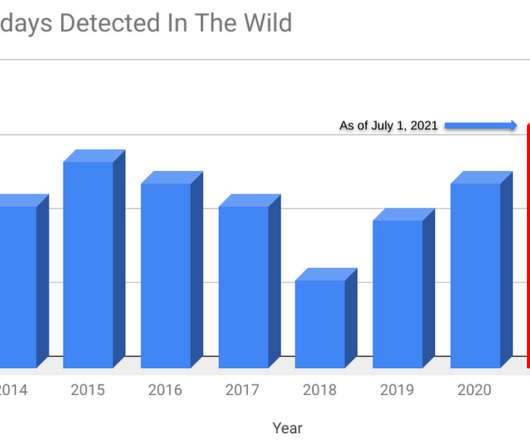
Security Affairs
JULY 14, 2021
Google security experts revealed that Russia-linked APT group targeted LinkedIn users with Safari zero-day. Security researchers from Google Threat Analysis Group (TAG) and Google Project Zero revealed that four zero-day vulnerabilities have been exploited in the wild earlier this year. The four security flaws were discovered earlier this year and affect Google Chrome, Internet Explorer, and WebKit browser engine.

Data Breach Today
JULY 15, 2021
'Tortoiseshell' Group Used the Social Network to Contact Targets Facebook's threat intelligence team says it has disrupted an Iranian advanced persistent threat group that was using the social network as part of an effort to spread malware and conduct cyberespionage operations, primarily in the U.S.

Schneier on Security
JULY 14, 2021
China is making sure that all newly discovered zero-day exploits are disclosed to the government. Under the new rules, anyone in China who finds a vulnerability must tell the government, which will decide what repairs to make. No information can be given to “overseas organizations or individuals” other than the product’s manufacturer.

AIIM
JULY 15, 2021
With SharePoint now included in Enterprise Microsoft 365 subscriptions, it is now more accessible than ever before. It is tempting for organizations to just jump right in and start setting it up without much forethought. SharePoint, however, is a sophisticated content management system. As a leader in the content management space, it offers a robust set of capabilities.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Security Affairs
JULY 15, 2021
HelloKitty ransomware gang is using a Linux variant of their malware to target VMware ESXi virtual machine platform. A Linux variant of the HelloKitty ransomware was employed in attacks against VMware ESXi systems. The move of the ransomware gang aims at expanding the operations targeting enterprises that are largely adopting virtualizing platforms.

Data Breach Today
JULY 13, 2021
Flaw in Serv-U File-Transfer Software Unconnected to Orion Supply-Chain Attack Attackers have been actively exploiting a zero-day flaw in SolarWinds' Serv-U Managed File Transfer Server and Serv-U Secured FTP software, the security software vendor warns. SolarWinds has released patched versions that mitigate the flaw, discovered by Microsoft, and is urging users to update.

Hunton Privacy
JULY 15, 2021
The California Attorney General has updated its CCPA FAQs to state that the newly developed Global Privacy Control (“GPC”) “must be honored by covered businesses as a valid consumer request to stop the sale of personal information.”. This change appears to draw on Section 999.315(c) of the CCPA regulations, which states that “[i]f a business collects personal information from consumers online, the business shall treat user-enabled global privacy controls, such as a browser plug-in or privacy set

Schneier on Security
JULY 13, 2021
Interesting attack : Masquerading as UK scholars with the University of London’s School of Oriental and African Studies (SOAS), the threat actor TA453 has been covertly approaching individuals since at least January 2021 to solicit sensitive information. The threat actor, an APT who we assess with high confidence supports Islamic Revolutionary Guard Corps (IRGC) intelligence collection efforts, established backstopping for their credential phishing infrastructure by compromising a legitima

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
JULY 16, 2021
The Joker malware is back, experts spotted multiple malicious apps on the official Google Play store that were able to evade scanners. Experts reported an uptick in malicious Android apps on the official Google Play store laced with the Joker mobile trojan. The Joker malware is a malicious code camouflaged as a system app and allows attackers to perform a broad range of malicious operations, including disable the Google Play Protect service , install malicious apps, generate fake reviews, and sh

Data Breach Today
JULY 16, 2021
Report: Cooperation Is Required to Protect US Critical Infrastructure A greater level of cooperation is needed between the DOD and DHS to ensure that U.S. critical infrastructure is protected against various cyberthreats, according to an inspector general's report. The SolarWinds attack showed the need for more coordination between the two departments.

eSecurity Planet
JULY 13, 2021
Email spoofing is a common tactic hackers use in phishing and social engineering attacks. Spoofing trends tend to increase around popular shopping holidays in the U.S., including Black Friday and Amazon Prime Day , and the recent LinkedIn data scrape has already led to an uptick in spoofing attempts. With these threats in mind, it’s important to understand how spoofing works and what you can do to protect yourself, your employees, and your business from falling victim to a spoofing attack.

Dark Reading
JULY 13, 2021
More than half of enterprises surveyed for Dark Reading's State of Malware Threats report indicate they are making at least a few changes to their supply chain security defenses following recent attacks on software vendors such as SolarWinds.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
JULY 15, 2021
Security researchers have linked a new ransomware strain called Diavol to the Wizard Spider threat group behind the Trickbot botnet. BleepingComputer noted the ransomware families utilize the same I/O operations for file encryption queueing and use nearly identical command-line parameters for the same functionality. There may be some similarities, but as they’ve explained and SpearTip has validated, there are two interesting differences that make the direct connection improbable.

Data Breach Today
JULY 10, 2021
The oil and gas industry is yet again a victim of Agent Tesla malware A sophisticated campaign that uses remote access Trojans and malware-as-a-service threats for cyber espionage purposes has been targeting large international energy companies for at least a year, according to cybersecurity company Intezer.
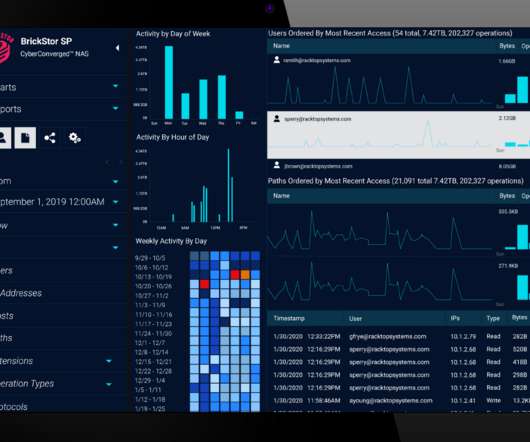
eSecurity Planet
JULY 12, 2021
While many cybersecurity vendors approach zero trust from the perspective of microsegmentation , shrinking the network as much as possible, one startup thinks security needs to be as close to the data as possible and is thus focused on data storage. Maryland-based RackTop Systems boasts a Department of Defense (DoD) pedigree, giving its founders a vantage point into the challenges that high-security environments face.

Data Protection Report
JULY 16, 2021
On July 6, 2021, Connecticut enacted a new law (Public Act 21-119) that creates a safe harbor for companies that followed certain cybersecurity protocols in the event there’s a security breach. The new Connecticut law is similar to the one Ohio enacted in 2018. Both laws apply to “covered entities” that possess “personal information” and suffer a “breach of security of the system” under that state’s data breach notification law.

Advertisement
Start-ups & SMBs launching products quickly must bundle dashboards, reports, & self-service analytics into apps. Customers expect rapid value from your product (time-to-value), data security, and access to advanced capabilities. Traditional Business Intelligence (BI) tools can provide valuable data analysis capabilities, but they have a barrier to entry that can stop small and midsize businesses from capitalizing on them.
Security Affairs
JULY 12, 2021
Researchers from Cyber News Team have spotted threat actors offering for sale 600 million LinkedIn profiles scraped from the platform, again. Original post: [link]. For the third time in the past four months, LinkedIn seems to have experienced another massive data scrape conducted by a malicious actor. Once again, an archive of data collected from hundreds of millions of LinkedIn user profiles surfaced on a hacker forum, where it’s currently being sold for an undisclosed sum.

Data Breach Today
JULY 11, 2021
On-Premises Software Patched, SaaS to Come Online Again Miami-based software company Kaseya released patches on Sunday for its monitoring and management software that was exploited by a ransomware group. The patches take care of the last three vulnerabilities out of seven reported to Kaseya in early April but had yet to be fixed.

Elie
JULY 15, 2021
Learn the concepts behind deep-learning side-channels attack, a powerful cryptanalysis technique, by using it to recover AES cryptographic keys from a hardware device.

eSecurity Planet
JULY 16, 2021
With major cybersecurity incidents an almost daily occurrence, organizations need an incident response plan for the likelihood that they will someday be breached. And more than ever, they also need an incident response service that can step in to help clean up those messes. Despite all the cybersecurity defenses in enterprises, the human element matters the most, as phishing attacks remain the top avenue of incursion, accounting for more than 85% of all breaches, according to the annual Verizon

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Security Affairs
JULY 10, 2021
Mint Mobile discloses a data breach, an unauthorized attacker gained access to subscribers’ account information and ported phone numbers. Mint Mobile is an American telecommunications company which sells mobile phone services and operates as an MVNO on T-Mobile’s cellular network in the United States. BleepingComputer reported that Mint Mobile has disclosed a data breach that exposed subscribers’ account information and ported phone numbers to another carrier.

Data Breach Today
JULY 16, 2021
Company Also Plans to Upgrade All Page Loads to HTTPS Google will soon release a security update to address eight vulnerabilities in its Chrome browser, including a high-severity zero-day flaw that's being exploited in the wild. It also plans to upgrade all Chrome page loads to HTTPS.

Threatpost
JULY 14, 2021
The Joker premium billing-fraud malware is back on Google Play in a fresh onslaught, with an updated bag of tricks to evade scanners.
Let's personalize your content