SolarWinds Hires Chris Krebs to Reboot Its Cybersecurity
Data Breach Today
JANUARY 8, 2021
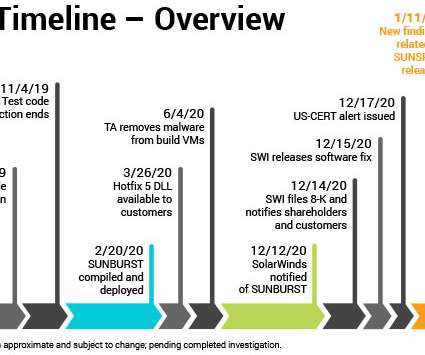
Hacked Firm Also Taps Former Facebook CSO as It Responds to Supply Chain Attack As security software firm SolarWinds investigates the supply chain attack involving its Orion software and looks to rebuild its security processes and reputation, it's hired former U.S. cybersecurity czar Chris Krebs and former Facebook CSO Alex Stamos as advisers.




































Let's personalize your content