MetaMask Crypto Wallet Phishing
KnowBe4
JUNE 27, 2022
A phishing campaign attempting to steal credentials for MetaMask cryptocurrency wallets, according to Lauryn Cash at Armorblox.

KnowBe4
JUNE 27, 2022
A phishing campaign attempting to steal credentials for MetaMask cryptocurrency wallets, according to Lauryn Cash at Armorblox.

Data Breach Today
JUNE 27, 2022
Baptist Medical Center Latest on Growing List of Entities Reporting Major Hacks A malware incident involving exfiltration of data has affected more than 1.24 million patients of Texas-based Baptist Medical Center and Resolute Health Hospital. It adds to a growing list of major health data breaches reported to regulators in recent weeks as affecting millions of individuals.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 27, 2022
Vulnerabilities in web applications are the leading cause of high-profile breaches. Related: Log4J’s big lesson. Log4j, a widely publicized zero day vulnerability, was first identified in late 2021, yet security teams are still racing to patch and protect their enterprise apps and services. This notorious incident highlights the security risks associated with open-source software, and the challenges of protecting web applications against zero day attacks.

Data Breach Today
JUNE 27, 2022
FIDO Alliance Leader Andrew Shikiar on New Deal With Google, Apple and Microsoft Tired of keeping track of passwords? Recent announcements by major platform vendors Google, Apple and Microsoft could have passwords down for the count in the next six years, says Andrew Shikiar, executive director of the FIDO Alliance, which has been on a 10-year mission to eliminate passwords.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Data Matters
JUNE 27, 2022
Last week, the UK Competition and Markets Authority (CMA) hosted its inaugural Data, Technology, and Analytics (DaTA) Conference. The CMA DaTa Conference has been hailed as a milestone as it convened for the first time regulators, data scientists, engineers, tech companies, and academics to discuss evolving challenges in digital markets. The conference coincided with London Tech Week, during which Chris Philp, UK Minister for Tech and the Digital Economy, unveiled a new UK Digital Strategy: the
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
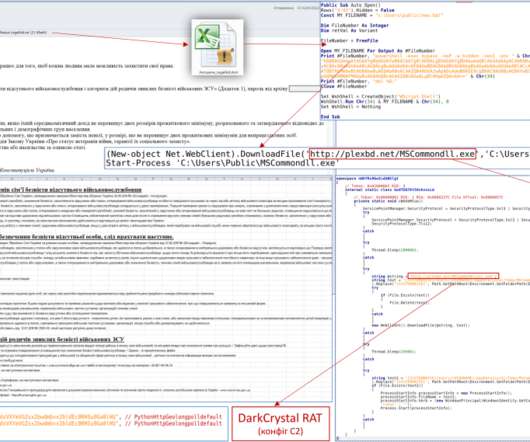
Security Affairs
JUNE 27, 2022
The Ukrainian CERT-UA warns of attacks against Ukrainian telecommunications operators involving the DarkCrystal RAT. The Governmental Computer Emergency Response Team of Ukraine (CERT-UA) is warning of a malware campaign targeting Ukrainian telecommunications operators with the DarkCrystal RAT. The malspam messages have the topic “Free primary legal aid” use a password-protected attachment “Algorithm of actions of members of the family of a missing serviceman LegalAid.rar.̶

Data Breach Today
JUNE 27, 2022
Criminals Offer $1,000 to $1M for Vulnerabilities Ransomware-as-a-service gang LockBit has set up a bug bounty program for its malware and for exploitable vulnerabilities it could use to further criminal activities. Whether the program will go as planned is an open question. The gang is offering $1,000 to $1 million in remuneration.
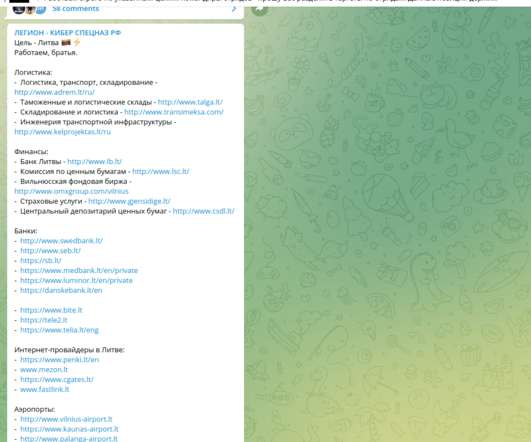
Security Affairs
JUNE 27, 2022
Lithuania confirmed it had been hit by an “intense” cyberattack, after Vilnius imposed restrictions on the rail transit of certain goods to Kaliningrad. The government of Lithuania announced on Monday that it had been hit by an “intense” cyberattack, likely launched from Moscow, days after the Russian government protested restrictions Vilnius imposed on the rail transit of certain goods to Kaliningrad.

Data Breach Today
JUNE 27, 2022
Hackers Also Claim Attack on 2 Other Steel Manufacturers Hacking group Gonjeshke Darande, or Predatory Sparrow in Persian, is claiming responsibility for hacking Iranian manufacturer Khouzestan Steel Company. The company shut down operations, but semiofficial Mehr News Agency reports that the factory is expected to return to normal by the end of today.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Hunton Privacy
JUNE 27, 2022
On June 16, 2022, the Federal Trade Commission issued a report to Congress titled Combatting Online Harms Through Innovation (the “Report”) that urges policymakers and other stakeholders to exercise “great caution” about relying on artificial intelligence (“AI”) to combat harmful online content. The Report comes after Congress in the 2021 Appropriations Act directed the FTC to examine ways that AI may be used to address a wide variety of specified harmful online content such as scams, deepfakes,

Data Breach Today
JUNE 27, 2022
Infosys CISO Vishal Salvi on Mentoring, Online Training and Foundational Skills The gap between cybersecurity workforce demand and the number of skilled workers available to fill those jobs widened during the pandemic. So organizations need to take a multi-pronged approach to attract, reskill and retain employees, says Vishal Salvi, CISO and head of cyber practice at Infosys.

DLA Piper Privacy Matters
JUNE 27, 2022
The Italian privacy authority, the Garante, deemed that the use of Google Analytics results in unlawful transfers of personal data to the United States in violation of the principles outlined in the Schrems II ruling. In Order No. 224 of June 9, 2022 , the Italian data protection authority found that transfers of personal data to the United States by an Italian website through the use of Google Analytics violates the GDPR.

Data Breach Today
JUNE 27, 2022
Company Says the 55 Layoffs Will Boost Efficiency, Cut Expenses and Preserve Cash IronNet is laying off 17% of its employees in a cost-cutting effort just 10 months after going public by merging with a special purpose acquisition company. The 55 layoffs will occur by the end of June and the company will spend the $1 million allocated for severance and other termination benefits.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
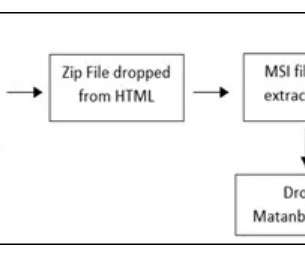
Security Affairs
JUNE 27, 2022
Matanbuchus malware-as-a-service (Maas) has been observed spreading through phishing campaigns, dropping Cobalt Strike beacons. Threat intelligence firm Cyble has observed a malware-as-a-service (Maas), named Matanbuchus, involved in malspam attacks dropping Cobalt Strike beacons. Matanbuchus is a malware loader that first appeared on the threat landscape in February 2021, when it was offered for rent on Russian-speaking cybercrime forums at a price of $2500.

Data Breach Today
JUNE 27, 2022
Airgap CEO Ritesh Agrawal on Reducing On-Premises and Remote Work Security Friction The move to remote working has created two sets of tools, policies and personnel that are making it harder for security teams to protect the enterprise, says Airgap Networks CEO and co-founder Ritesh Agrawal. He discusses how Airgap is addressing the challenges of hybrid work.

Security Affairs
JUNE 27, 2022
Iranian state-owned Khuzestan Steel Company was hit by a cyber attack that forced the company to halt its production. The Khuzestan Steel Company is one of the major steel companies owned by the Iranian government. The company was forced to halt production due to a cyberattack. According to the Associated Press , Khuzestan Steel Company has a monopoly on steel production in Iran along with two other major state-owned firms.

Data Breach Today
JUNE 27, 2022
Gonz Gonzales, CISO of JG Summit Holdings, Discusses His PAM Journey How does a conglomerate implement PAM across multiple companies? What are some of the challenges, and how can you overcome them? Gonz Gonzales, the CISO at JG Summit Holdings, one of the largest conglomerates in the Philippines, shares his journey of PAM implementation across companies.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

OpenText Information Management
JUNE 27, 2022
Customers trust OpenText™ Documentum™ to help them ensure their high volume, critical business content is secure, organized, preserved and easily accessible while adhering to privacy and security protocols. Documentum users are also extending the value of their content to the cloud, simplifying access for content creation and collaboration, driving productivity improvements with easy-to-understand and personalized … The post What’s new in OpenText Documentum appeared first on OpenTex

Dark Reading
JUNE 27, 2022
NIST SP800-219 introduces the macOS Security Compliance Project (mSCP) to assist organizations with creating security baselines and defining controls to protect macOS endpoints.

Security Affairs
JUNE 27, 2022
CODESYS addressed 11 security flaws in the ICS Automation Software that could lead to information disclosure and trigger a denial-of-service (DoS) condition. CODESYS has released security patches to fix eleven 11 vulnerabilities in its ICS Automation Software. CoDeSys is a development environment for programming controller applications according to the international industrial standard IEC 61131-3.

Dark Reading
JUNE 27, 2022
If you haven't properly addressed the issue, you're already behind. But even if you've had a false start, it's never too late to get back up.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Micro Focus
JUNE 27, 2022
Micro Focus helps organizations run and transform their business at the same time, to achieve the critical elements of a successful digital transformation program.

Dark Reading
JUNE 27, 2022
Cerby platform emerges from stealth mode to let users automate security for applications outside of the standard IT purview.

IG Guru
JUNE 27, 2022
Check out the post here. The post Report: 73% of IT leaders say their company struggles with data retention costs via VentureBeat.com appeared first on IG GURU.

Dark Reading
JUNE 27, 2022
LockBit 3.0 promises to 'Make Ransomware Great Again!' with a side of cybercrime crowdsourcing.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

WIRED Threat Level
JUNE 27, 2022
If you use a mix of Apple, Android, and Windows gadgets, you're in luck: The security tool is now available to any Microsoft 365 subscriber.

Dark Reading
JUNE 27, 2022
Balancing public service with fraud prevention requires rule revisions and public trust.

Schneier on Security
JUNE 27, 2022
I did not attend WEIS this year , but Ross Anderson was there and liveblogged all the talks.
Let's personalize your content