Breached Data Indexer ‘Data Viper’ Hacked
Krebs on Security
JULY 13, 2020
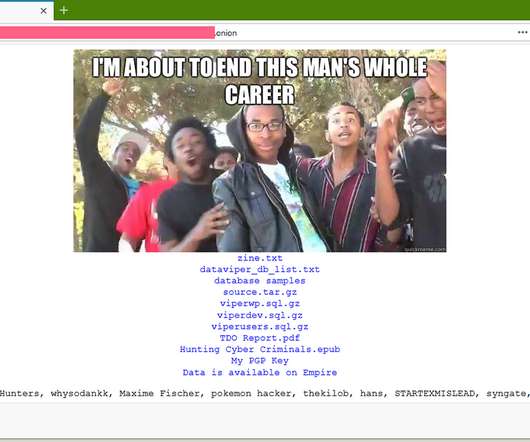
Data Viper , a security startup that provides access to some 15 billion usernames, passwords and other information exposed in more than 8,000 website breaches, has itself been hacked and its user database posted online. The hackers also claim they are selling on the dark web roughly 2 billion records Data Viper collated from numerous breaches and data leaks, including data from several companies that likely either do not know they have been hacked or have not yet publicly disclosed an intrusion.





































Let's personalize your content