Cybersecurity & Threat Modeling: Automated vs. Manual
Data Breach Today
SEPTEMBER 16, 2022
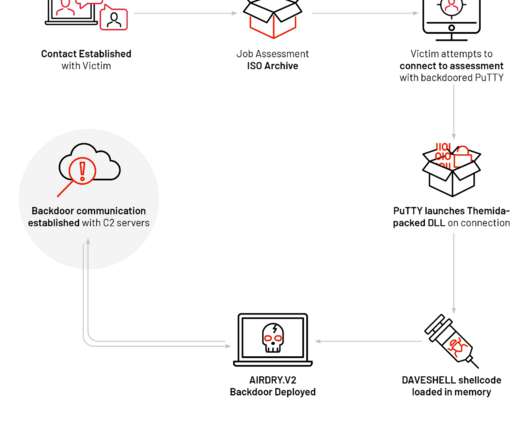
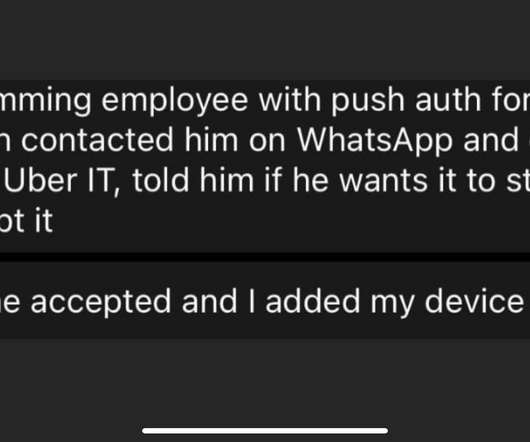
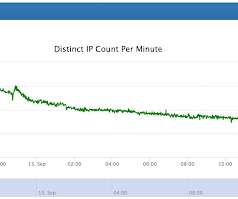
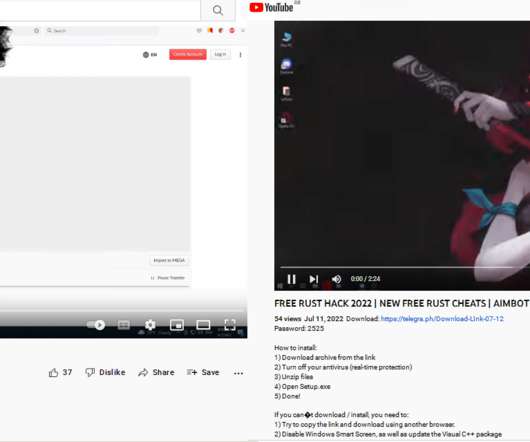
Cybersecurity threat modeling: automated tools or manual methods? It's not an either/or situation, say Stephen de Vries, CEO and co-founder of IriusRisk, and Adam Shostack of Shostack and Associates. Each approach brings unique business value, and they discuss the merits of both.





































Let's personalize your content