Introducing KnowBe4’s Password Policy E-Book
KnowBe4
JUNE 3, 2022
KnowBe4 just released its first e-book covering password attacks , defenses and what your password policy should be. Here is a summary of its recommendations:

 e-books
e-books 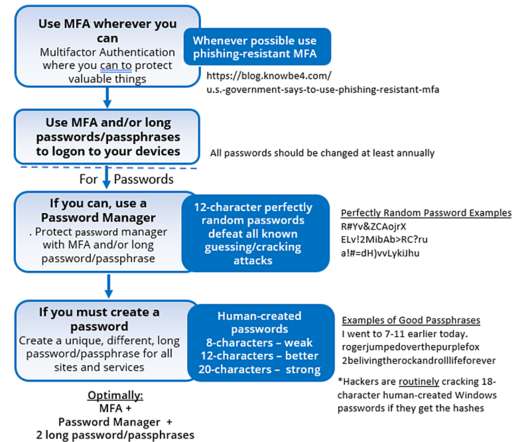
KnowBe4
JUNE 3, 2022
KnowBe4 just released its first e-book covering password attacks , defenses and what your password policy should be. Here is a summary of its recommendations:
Jamf
JANUARY 5, 2021
Jamf has written an e-book to help you learn more. The M1, Apple's new ARM-based chip, is not only the darling of tech reviewers. It's the start of a whole new era.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
AUGUST 3, 2018
Humble Bundle sells groups of e-books at ridiculously low prices, DRM free. This month , the bundles are all Wiley titles, including three of my books: Applied Cryptography , Secrets and Lies , and Cryptography Engineering. $15 15 gets you everything, and they're all DRM-free.
Data Breach Today
OCTOBER 15, 2020
System Housing Customer Data Accessed; Company Takes Down Nook E-Book Platform Books retailer Barnes & Noble is investigating a security incident involving unauthorized access to its corporate systems, including those storing customers' information.

Advertisement
That’s what drove the five companies in this e-book to change their approach to analytics. Download this e-book to learn about the unique problems each company faced and how they achieved huge returns beyond expectation by embedding analytics into applications.

CILIP
OCTOBER 7, 2020
New book explores the social, institutional and user impacts of e-legal deposit. Although a growing international activity, there has been little consideration of the impact of e-legal deposit on the 21st Century library, or on its present or future users. s Literature (Cambridge University Press 2018).

Schneier on Security
APRIL 2, 2024
And a 1994 review of Applied Cryptography by redacted : Applied Cryptography, for those who don’t read the internet news, is a book written by Bruce Schneier last year. The book is destined for commercial success because it is the only volume in which everything linked to cryptography is mentioned. There are many redactions.

Advertisement
This e-book details a number of graphics libraries plus a few bonus tools to modernize your embedded dashboards. If your embedded analytics are looking stale, leverage these free graphics libraries to take your embedded analytics offerings above and beyond.

Advertisement
Based on insights derived from industry professionals, this e-book uses first-hand experiences to help inform your analytics strategy. If you’ve been wondering how to invest in analytics, this research-based guide will take you through the 4 steps to finding the right solution for your application that will drive the most value.

Advertisement
This e-book describes the contrast in user experience between customizable self-service analytics and one-size-fits-all self-service analytics and what these options mean for your application and your business.

Advertisement
Think your customers will pay more for data visualizations in your application? Five years ago they may have. But today, dashboards and visualizations have become table stakes. Discover which features will differentiate your application and maximize the ROI of your embedded analytics. Brought to you by Logi Analytics.

Advertisement
Using a questionnaire that captures your unique needs, combined with a discussion of the identity verification landscape, this e-book should give you some needed perspective when searching for a provider.
Let's personalize your content