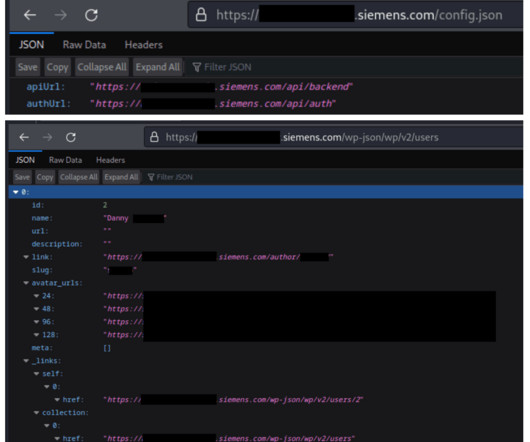
Don’t trust links with known domains: BMW affected by redirect vulnerability
Security Affairs
JANUARY 3, 2024
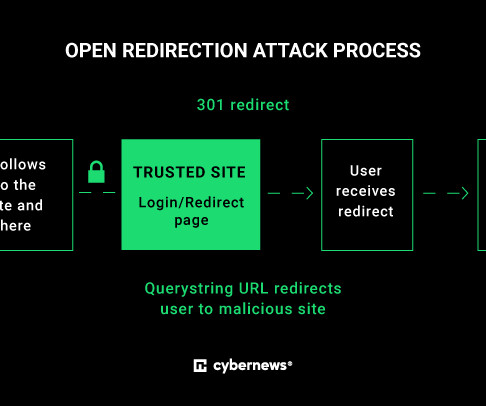
When the victim clicks on a link that appears to be legitimate, they’re redirected to the attacker’s website, where malicious JavaScript is executed in the client’s browser or where they are prompted to enter sensitive information. BMW is a German manufacturer of luxury vehicles headquartered in Munich.
































Let's personalize your content