Protecting Sensitive Data with Luna Key Broker for Microsoft Double Key Encryption
Thales Cloud Protection & Licensing
APRIL 1, 2021
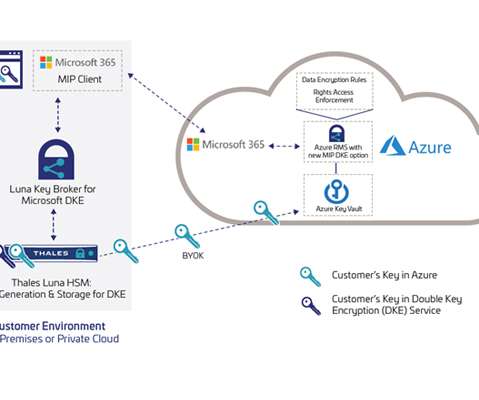
Protecting Sensitive Data with Luna Key Broker for Microsoft Double Key Encryption. Today’s remote working environment relies heavily on the collaborative sharing of information, challenging organizations to maintain the security of confidential data and regulatory compliance while driving employee productivity.














































Let's personalize your content